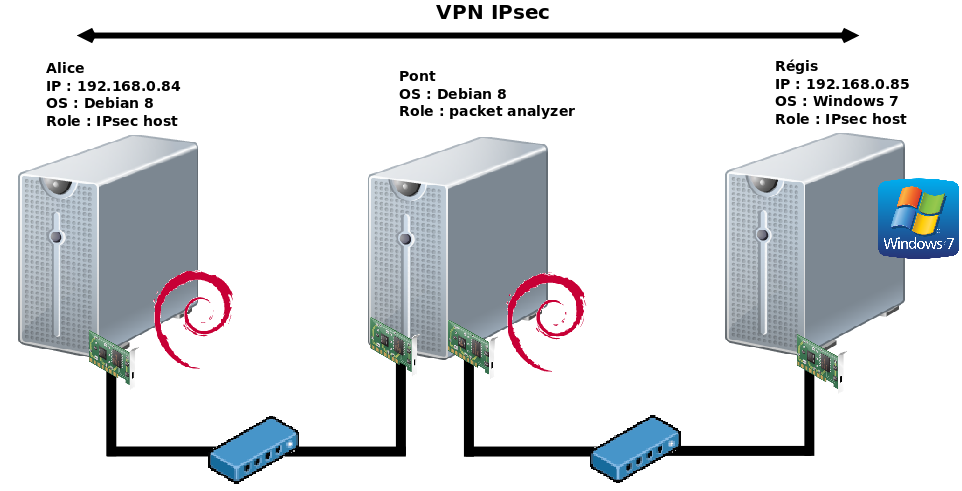
On créer un répertoire qui contiendra les certificats dans /var/certs :
root@host:~# cd /var/; mkdir certs; cd certs/; mkdir v01; cd v01/
NB : C'est le fichier /usr/lib/ssl/openssl.cnf qui permet de pré-remplir les infos du certificat (Country Name, State Or Privince etc...).
On créer son autorité de certification grâce au script /usr/lib/ssl/misc/CA.pl :
root@host:~# /usr/lib/ssl/misc/CA.pl -newca
CA certificate filename (or enter to create)
aking CA certificate ...
Generating a 1024 bit RSA private key
.............................................++++++
............++++++
writing new private key to './demoCA/private/cakey.pem'
Enter PEM pass phrase:
Verifying - Enter PEM pass phrase:
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:FR
State or Province Name (full name) [Some-State]:MP
Locality Name (eg, city) []:MARS
Organization Name (eg, company) [Internet Widgits Pty Ltd]:SOCIETE
Organizational Unit Name (eg, section) []:
Common Name (eg, YOUR name) []:RootCA
Email Address []:admin@societe.fr
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
Using configuration from /usr/lib/ssl/openssl.cnf
Enter pass phrase for ./demoCA/private/cakey.pem:
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number:
d9:34:84:c4:17:20:26:8b
Validity
Not Before: Oct 1 13:41:51 2012 GMT
Not After : Oct 1 13:41:51 2015 GMT
Subject:
countryName = FR
stateOrProvinceName = MP
organizationName = SheBang
commonName = RootCA
emailAddress = admin@societe.fr
X509v3 extensions:
X509v3 Subject Key Identifier:
B4:B6:FD:F4:33:62:76:B7:7B:3C:8A:18:9D:00:A4:0A:E0:5A:3C:DB
X509v3 Authority Key Identifier:
keyid:C4:B6:FD:F4:33:63:76:B7:7A:30:8A:18:9D:00:B4:0A:E0:5B:3C:DB
DirName:/C=FR/ST=MP/O=SheBang/CN=RootCA/emailAddress=admin@societe.fr
serial:D9:34:84:C4:17:20:26:8B
X509v3 Basic Constraints:
CA:TRUE
Certificate is to be certified until Oct 1 13:41:51 2015 GMT (1095 days)
Write out database with 1 new entries
Data Base Updated
root@host:~# apt-get install racoon ipsec-tools
root@host:~# openssl req -new -nodes -newkey rsa:1024 -sha1 -keyform PEM -keyout privkey.pem -outform PEM -out newreq.pem Generating a 1024 bit RSA private key .++++++ ..............++++++ writing new private key to 'privkey.pem' ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [AU]:FR State or Province Name (full name) [Some-State]:MP Locality Name (eg, city) []:MA_VILLE Organization Name (eg, company) [Internet Widgits Pty Ltd]:SheBang Organizational Unit Name (eg, section) []: Common Name (eg, YOUR name) []:VPN-Gateway-Debian Email Address []:admin@societe.fr Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []: An optional company name []:
root@host:~# /usr/lib/ssl/misc/CA.pl -sign Using configuration from /usr/lib/ssl/openssl.cnf Enter pass phrase for ./demoCA/private/cakey.pem: Check that the request matches the signature Signature ok Certificate Details: Serial Number: d9:34:84:c4:17:20:26:8c Validity Not Before: Oct 1 13:44:34 2012 GMT Not After : Oct 1 13:44:34 2013 GMT Subject: countryName = FR stateOrProvinceName = MP localityName = MARS organizationName = SheBang commonName = VPN-Gateway-Debian emailAddress = admin@societe.fr X509v3 extensions: X509v3 Basic Constraints: CA:FALSE Netscape Comment: OpenSSL Generated Certificate X509v3 Subject Key Identifier: 65:DF:0F:06:02:6F:34:8D:AB:63:E0:5B:1E:26:31:5E:B8:50:19:13 X509v3 Authority Key Identifier: keyid:B4:B6:FD:F4:33:62:76:B7:7A:30:8A:18:9D:00:A4:0A:E0:5B:3C:DB Certificate is to be certified until Oct 1 13:44:34 2013 GMT (365 days) Sign the certificate? [y/n]:y 1 out of 1 certificate requests certified, commit? [y/n]y Write out database with 1 new entries Data Base Updated Signed certificate is in newcert.pem
root@host:~# mkdir debian; mv newcert.pem newreq.pem privkey.pem -t debian/; cp debian/* /etc/racoon/certs
root@host:~# ln -s /var/certs/v01/demoCA/cacert.pem `openssl x509 -noout -hash -in /var/certs/v01/demoCA/cacert.pem`.0
user@alice # ls /etc/racoon/certs/ 3fda260d.0 cacert.pem newcert.pem privkey.pem
#path pre_shared_key "/etc/racoon/psk.txt";
path certificate "/etc/racoon/certs";
remote 192.168.0.85 {
exchange_mode main;
my_identifier asn1dn;
peers_identifier asn1dn;
verify_identifier on;
certificate_type x509 "newcert.pem" "privkey.pem";
proposal {
encryption_algorithm 3des;
hash_algorithm sha1;
authentication_method rsasig ;
dh_group 2;
}
}
sainfo address 192.168.0.84 any address 192.168.0.85 any {
#pfs_group modp768;
#pfs_group 2;
lifetime time 1 hour;
encryption_algorithm 3des;
authentication_algorithm hmac_sha1;
compression_algorithm deflate;
}
#!/usr/sbin/setkey -f
#
## Flush the SAD and SPD
flush;
spdflush;
#
spdadd 192.168.0.84 192.168.0.85 any -P out ipsec
esp/transport//require;
#
spdadd 192.168.0.85 192.168.0.84 any -P in ipsec
esp/transport//require;
#
user@alice # openssl req -new -nodes -newkey rsa:1024 -sha1 -keyform PEM -keyout privkey.pem -outform PEM -out newreq.pem Generating a 1024 bit RSA private key .................................++++++ ......++++++ writing new private key to 'privkey.pem' ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [AU]:FR State or Province Name (full name) [Some-State]:MP Locality Name (eg, city) []:MARS Organization Name (eg, company) [Internet Widgits Pty Ltd]:SOCIETE Organizational Unit Name (eg, section) []: Common Name (eg, YOUR name) []:Host-Windows Email Address []:admin@societe.fr Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []: An optional company name []:
user@alice # /usr/lib/ssl/misc/CA.pl -sign Using configuration from /usr/lib/ssl/openssl.cnf Enter pass phrase for ./demoCA/private/cakey.pem: Check that the request matches the signature Signature ok Certificate Details: Serial Number: d9:34:84:c4:17:20:26:8d Validity Not Before: Oct 1 13:48:48 2012 GMT Not After : Oct 1 13:48:48 2013 GMT Subject: countryName = FR stateOrProvinceName = MP localityName = MARS organizationName = SOCIETE commonName = Host-Windows emailAddress = admin@societe.fr X509v3 extensions: X509v3 Basic Constraints: CA:FALSE Netscape Comment: OpenSSL Generated Certificate X509v3 Subject Key Identifier: 3F:8B:22:32:82:01:3A:5A:F6:F4:67:70:BF:06:19:B4:FF:9A:6C:38 X509v3 Authority Key Identifier: keyid:B4:B6:FD:F4:33:62:76:B7:7A:30:8A:18:9D:00:A4:0A:E0:5B:3C:DB Certificate is to be certified until Oct 1 13:48:48 2013 GMT (365 days) Sign the certificate? [y/n]:y 1 out of 1 certificate requests certified, commit? [y/n]y Write out database with 1 new entries Data Base Updated Signed certificate is in newcert.pem
user@alice # openssl pkcs12 -export -inkey privkey.pem -in newcert.pem -certfile demoCA/cacert.pem -out export.p12 -name "Windows Cert" Enter Export Password: Verifying - Enter Export Password:
user@alice # ls -R debian demoCA export.p12 newcert.pem newreq.pem privkey.pem ./debian: newcert.pem newreq.pem privkey.pem ./demoCA: cacert.pem careq.pem certs crl crlnumber index.txt index.txt.attr index.txt.attr.old index.txt.old newcerts private serial serial.old ./demoCA/certs: ./demoCA/crl: ./demoCA/newcerts: D93484C41720268B.pem D93484C41720268C.pem D93484C41720268D.pem ./demoCA/private: cakey.pem
user@alice # setkey -FP
user@alice # racoon -F -f /etc/racoon/racoon.conf
user@alice # setkey -f /etc/ipsec-tools.conf
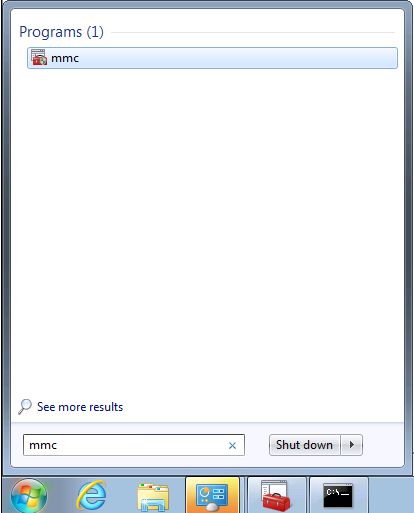
Ouverture de la Microsoft Management Console :
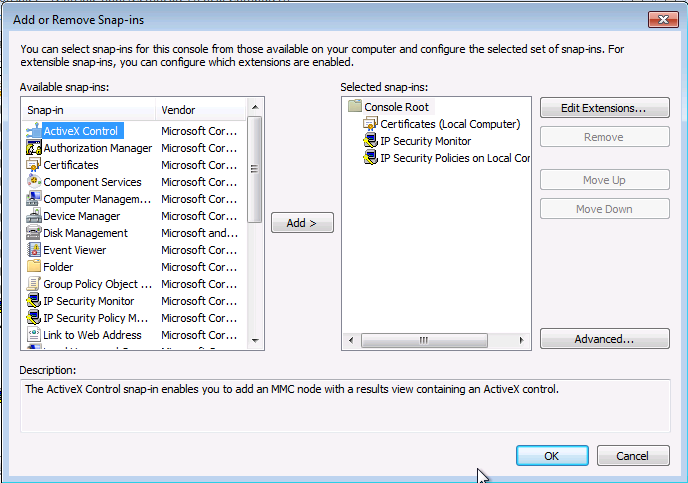
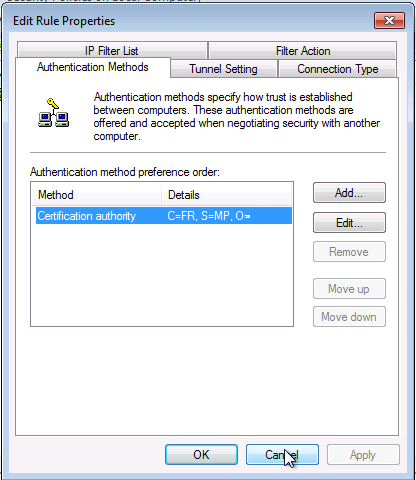
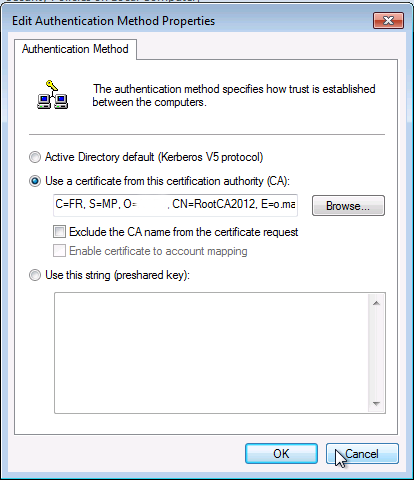
Et on rajoute les même informations que précisé ici
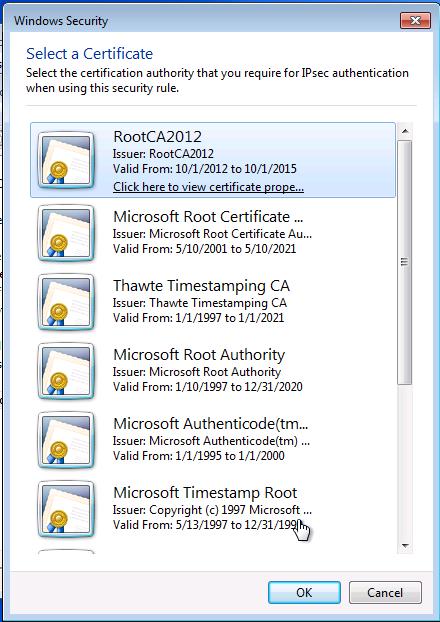
On installe le certificat
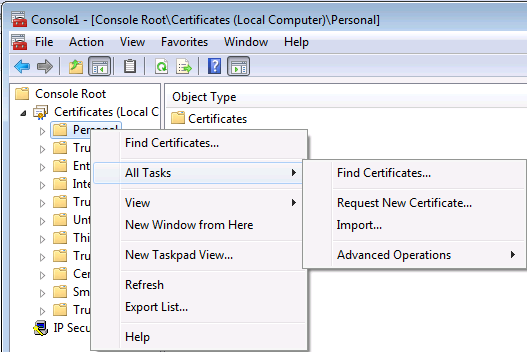
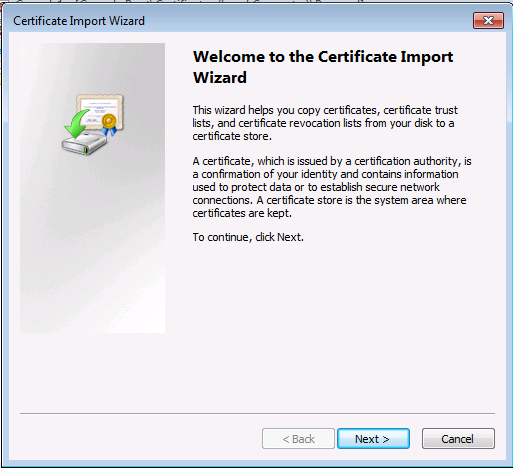
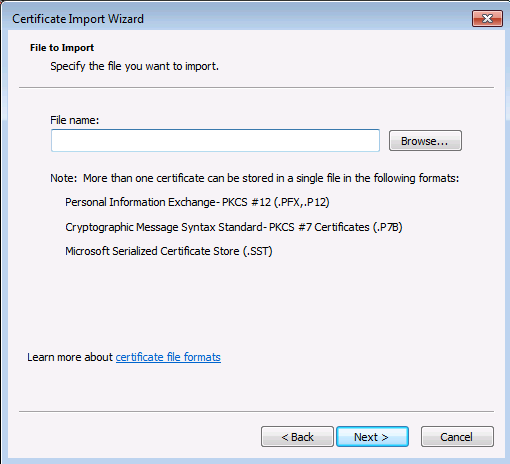
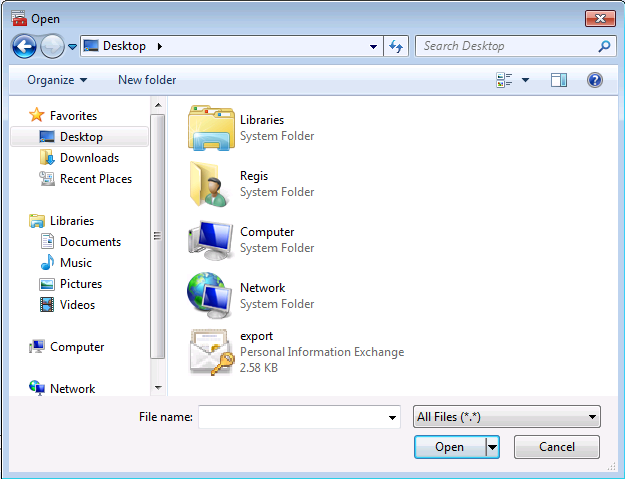
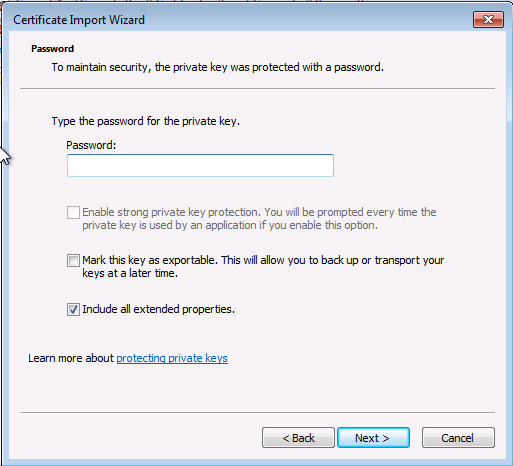
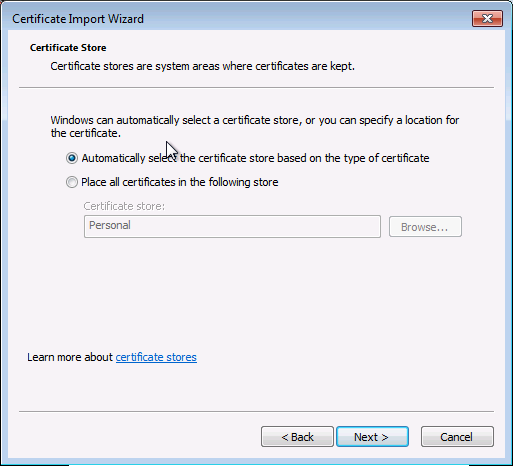
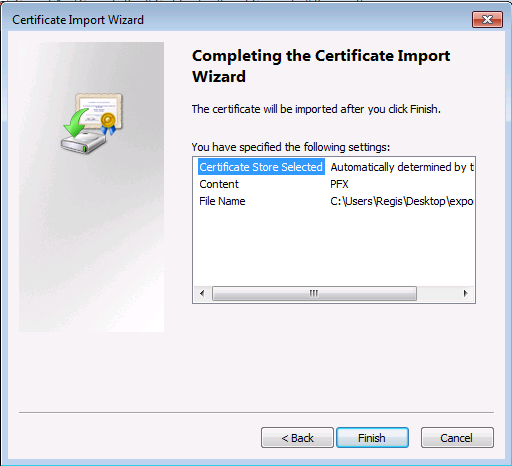
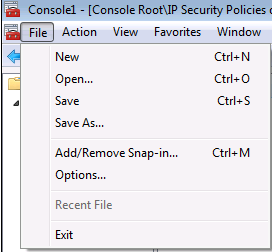
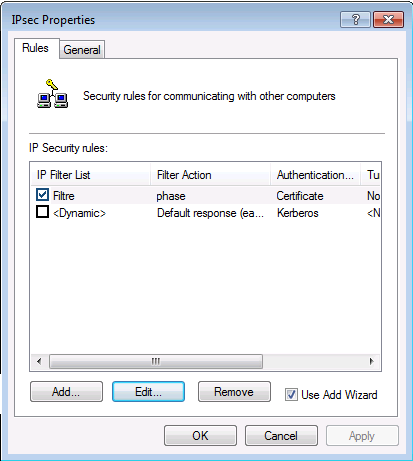
On retourne ensuite dans la console MMC :
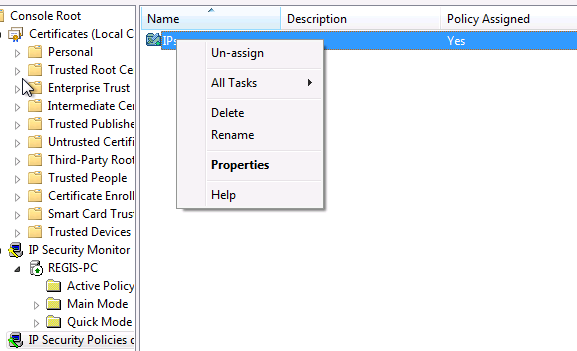
Contact :