MFA authentication is the new way to increase Users authentication security. It allows to reduce passwords compromission risk.
Indeed, MFA require multiple forms of verification to prove your identity when signing into an application.
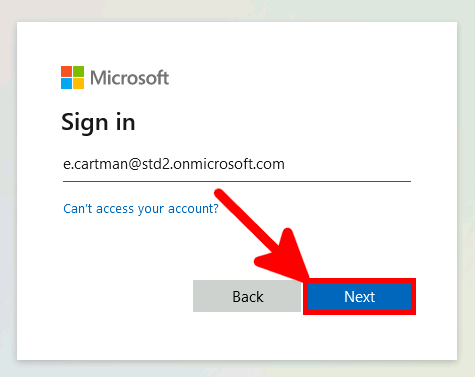
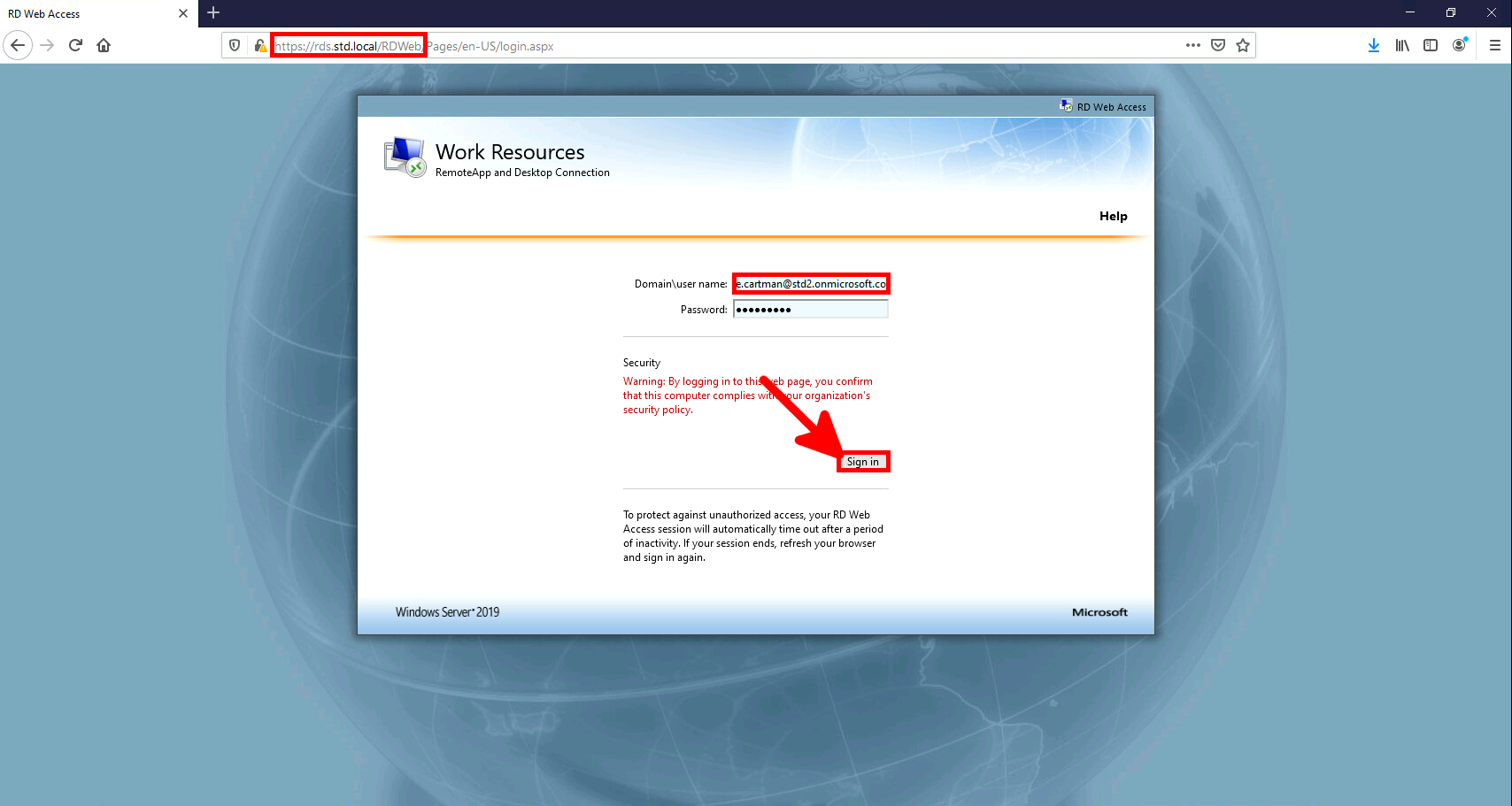
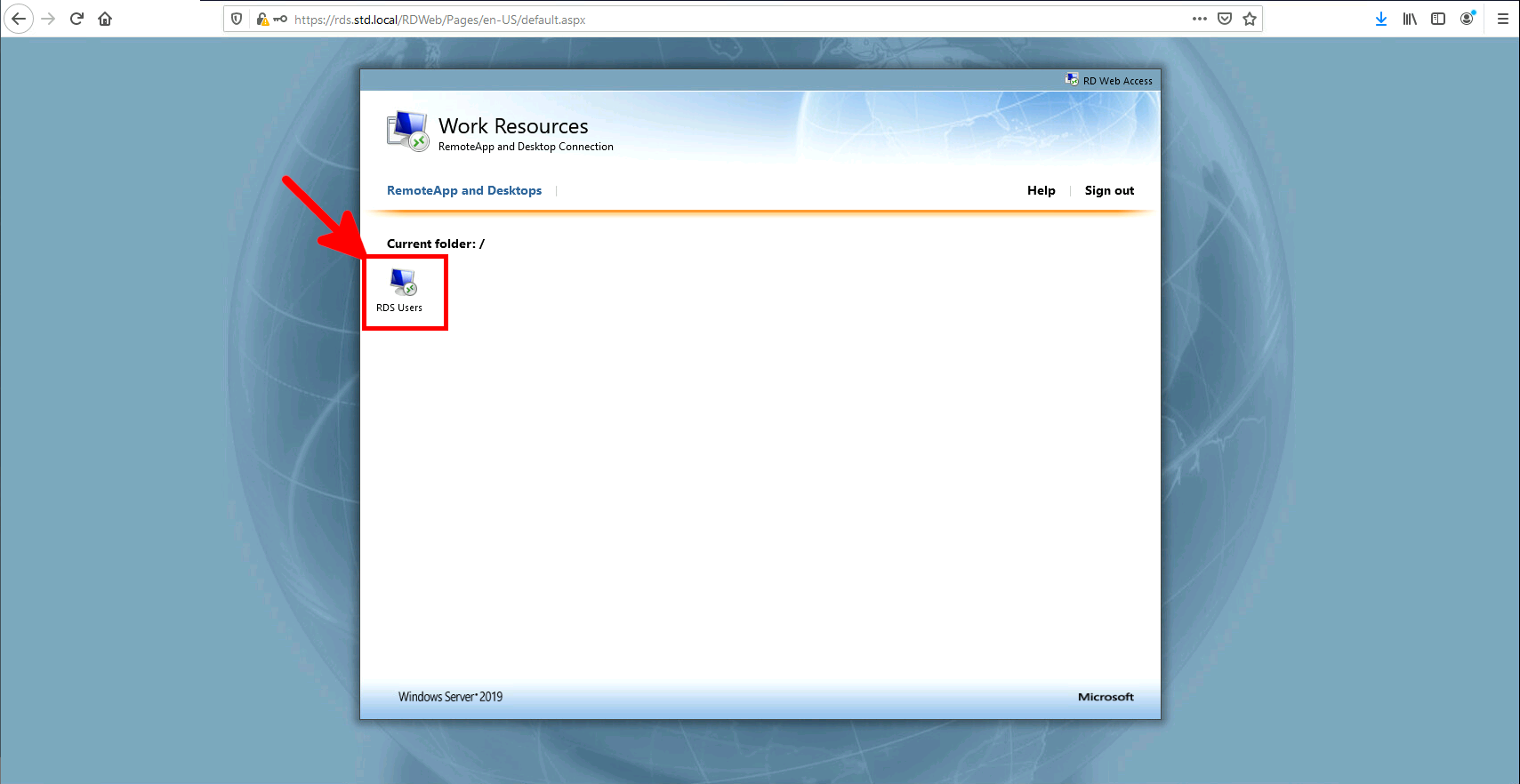
In this guide, we will see how to enable MFA for RDS users by using the Microsoft Authenticator app.
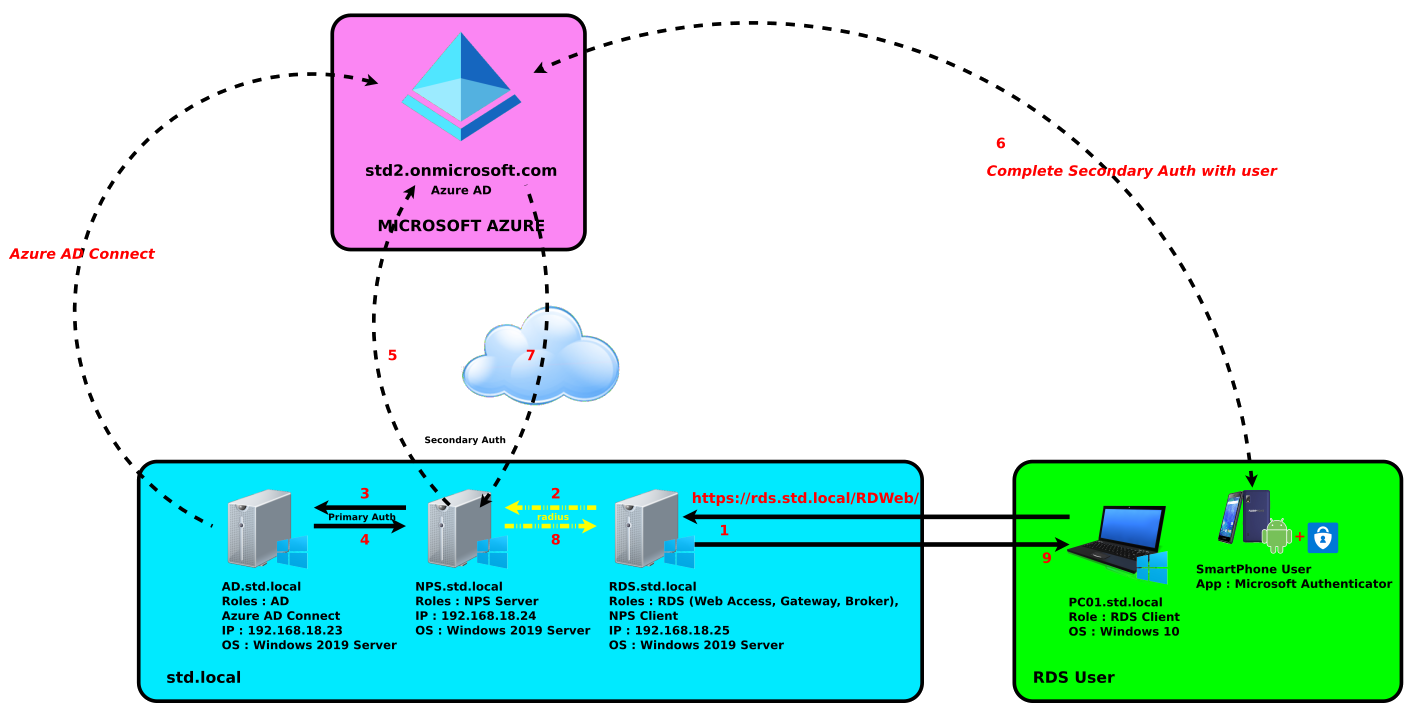
No surprise with Microsoft nothing very clear about licensing, but it seems we need a P1 or P2 license.
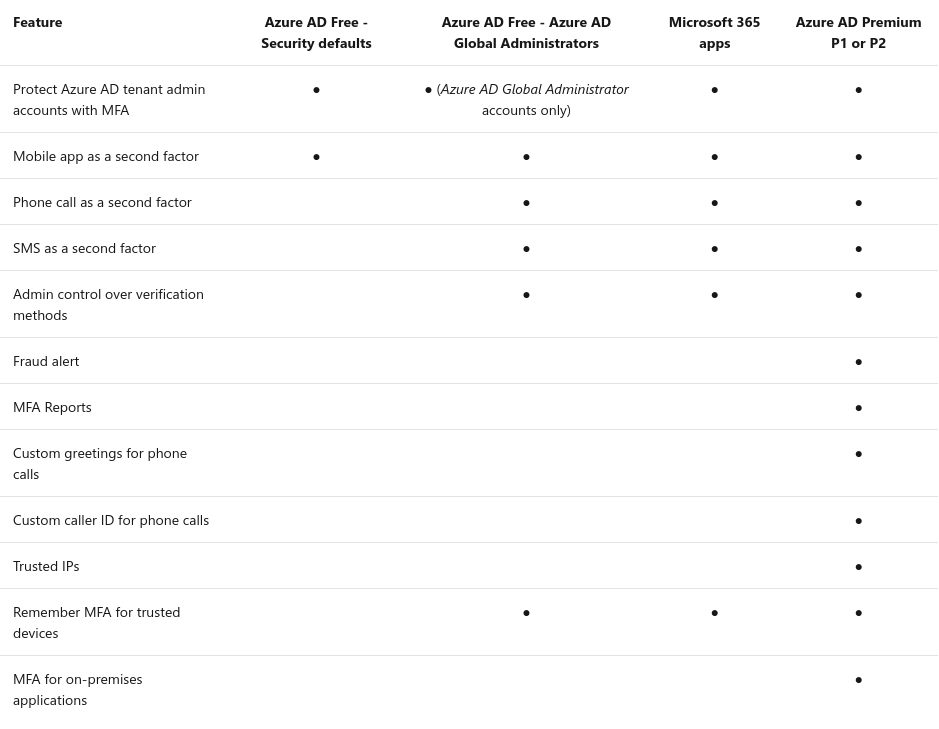
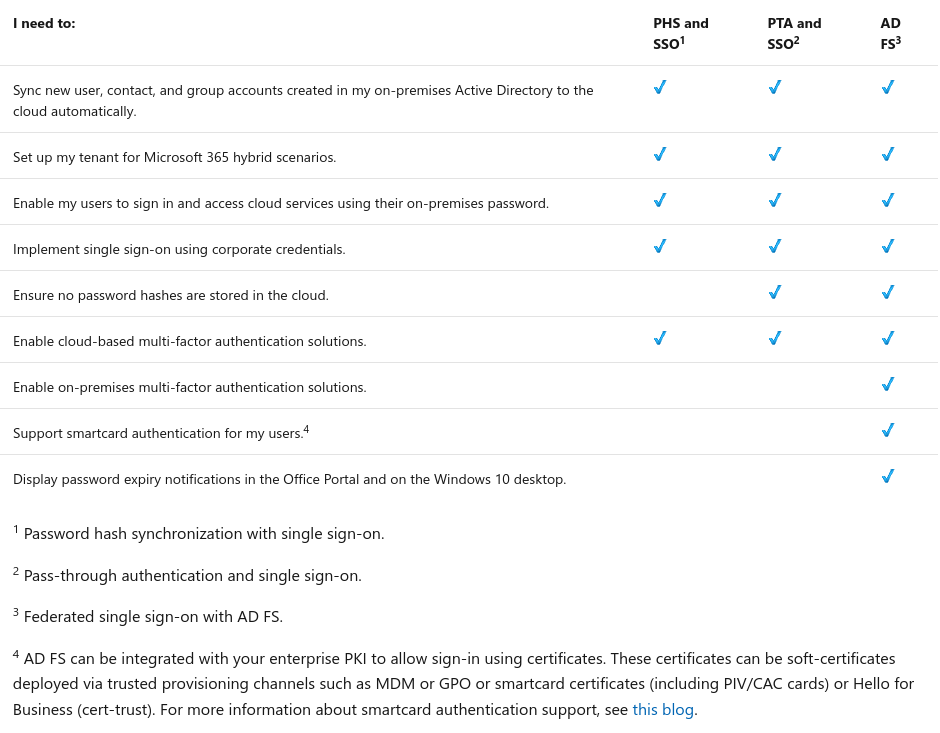
Not really clear neither but it seems we also need don't need a AD FS server : link.

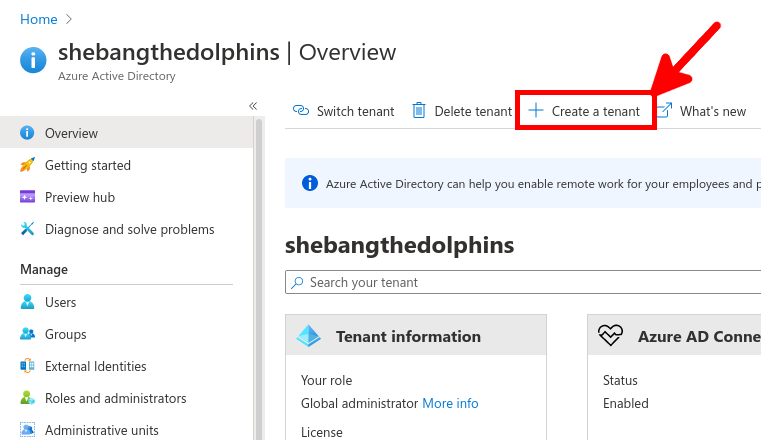
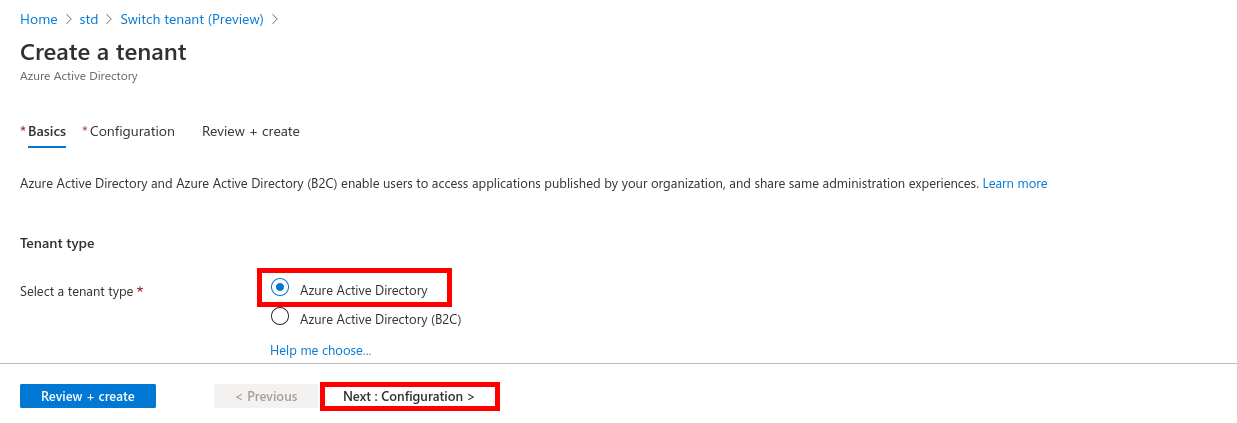
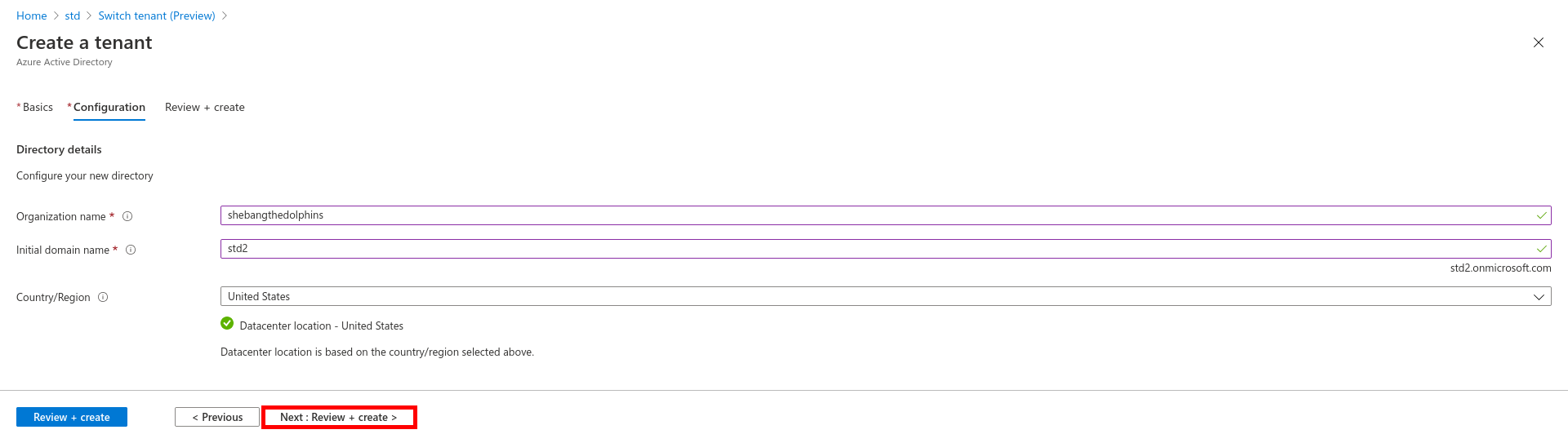
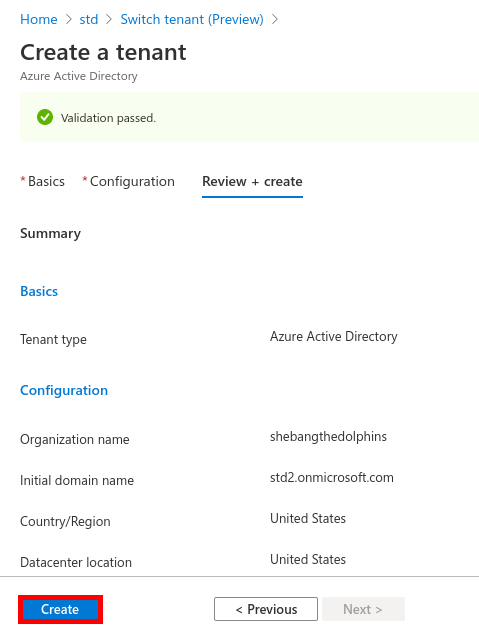
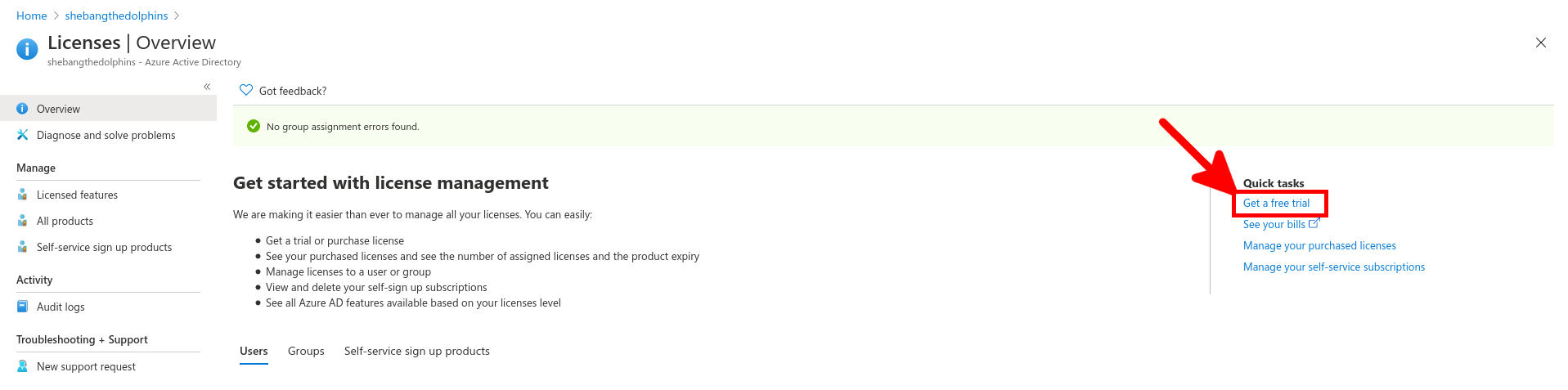
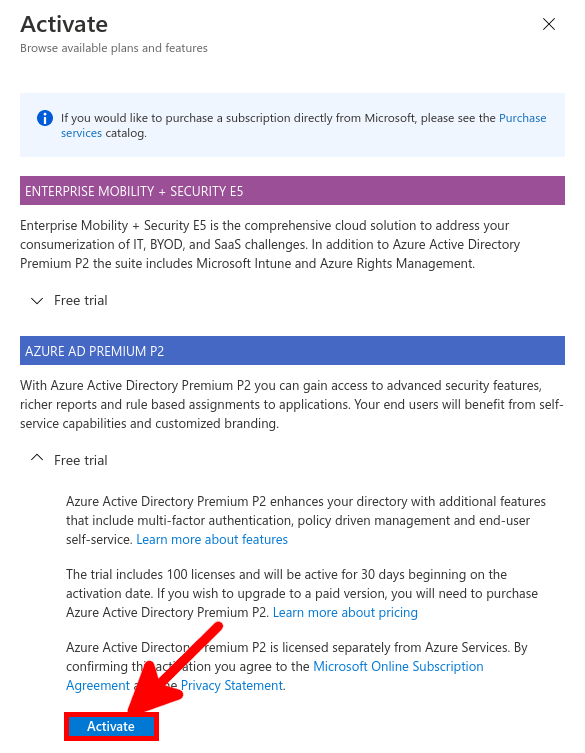
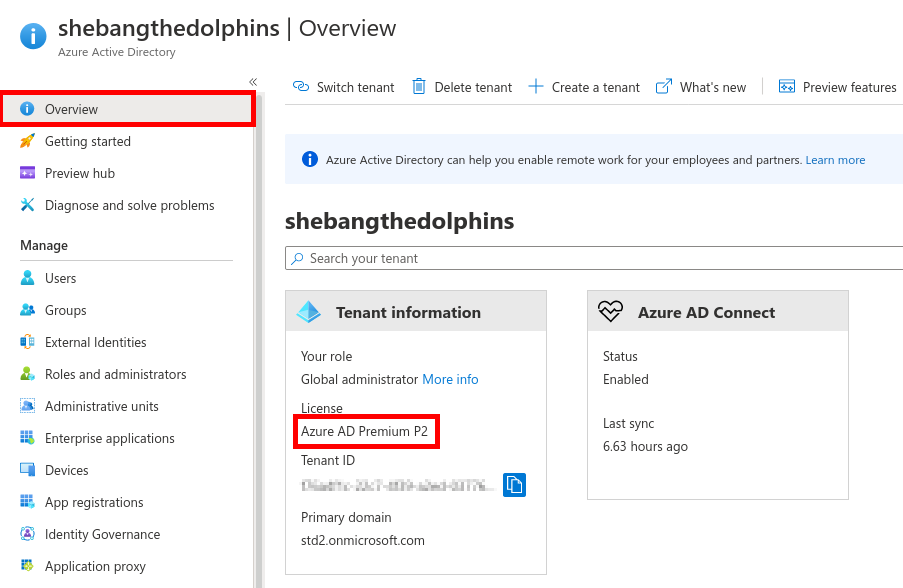
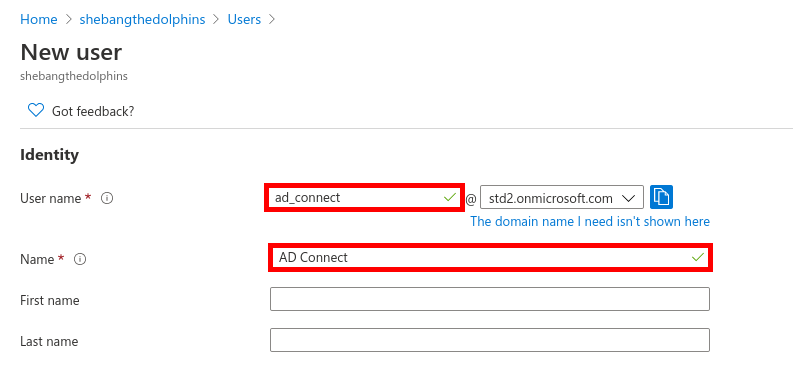
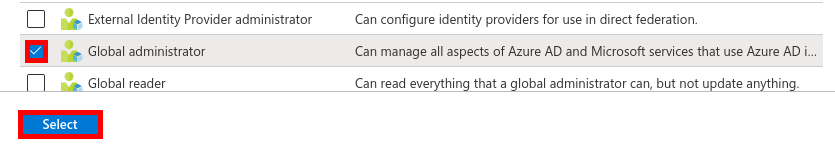
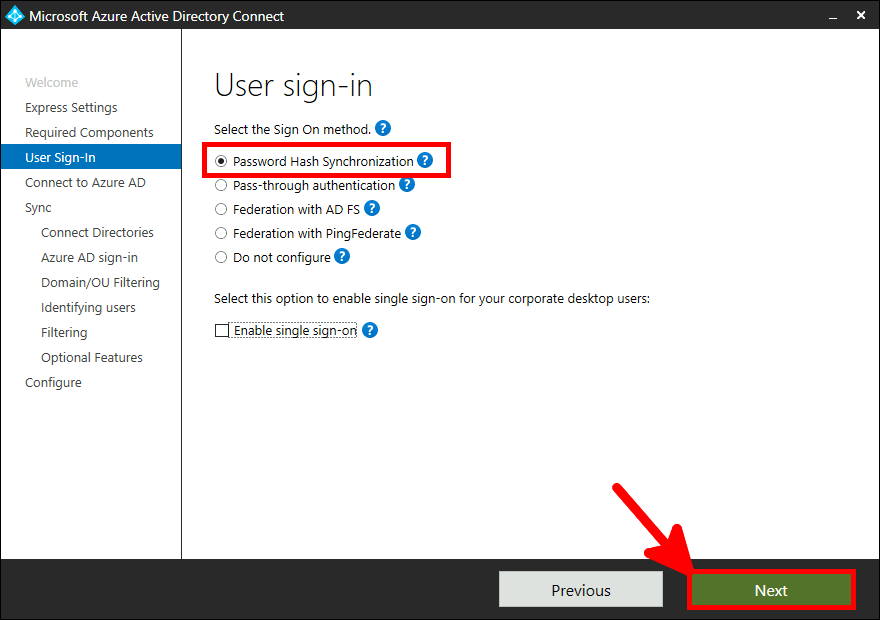
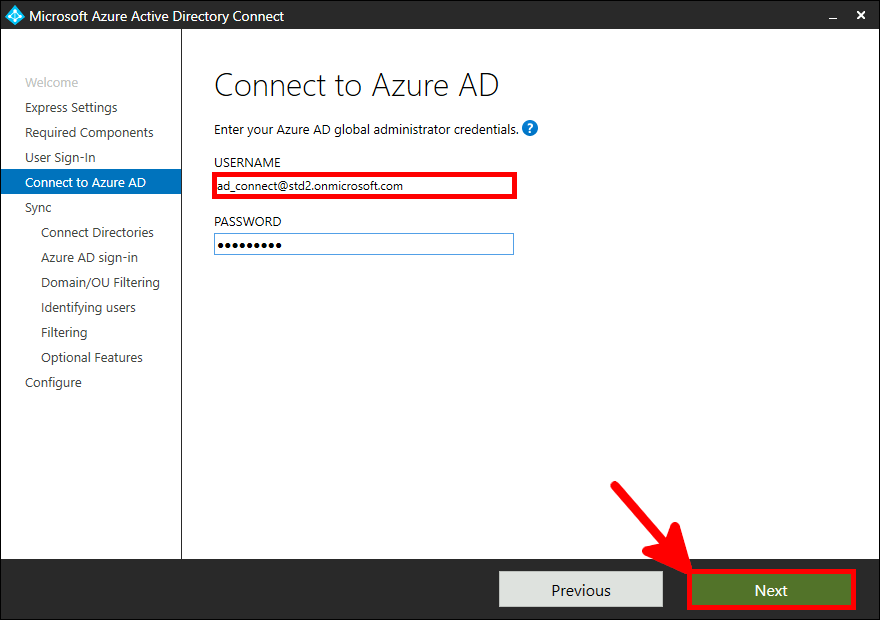
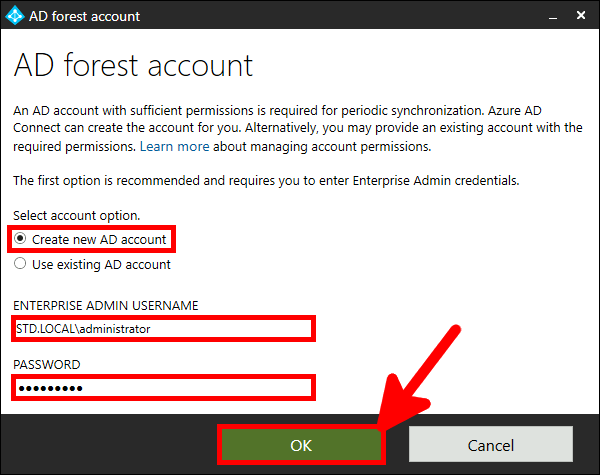
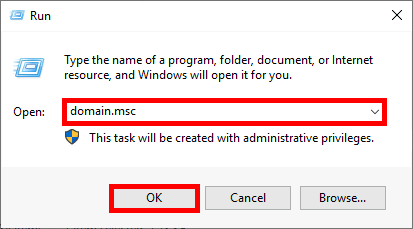
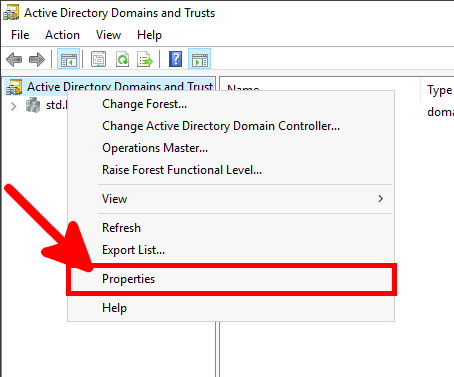
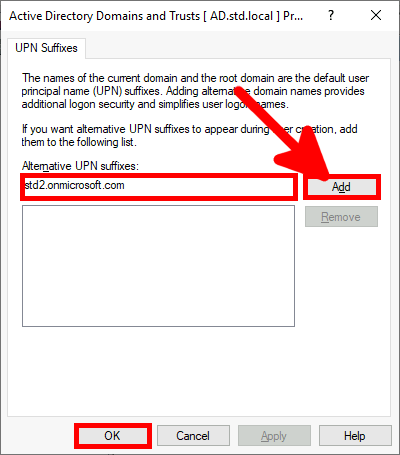
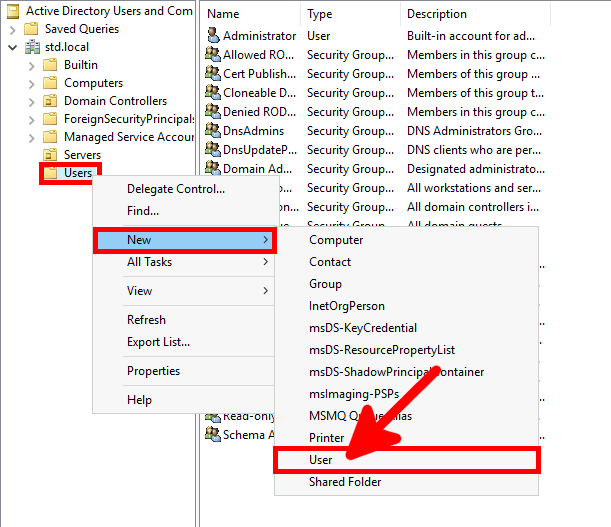
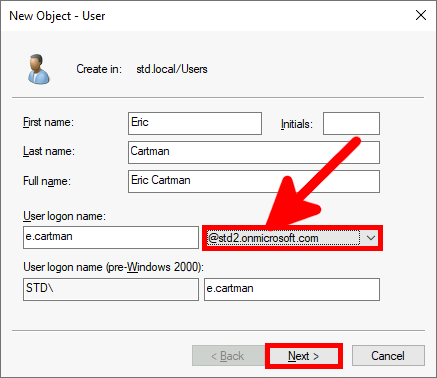
From the Azure portal we will create a New user account which will be used to sync our local AD (std.local) server with Azure AD (std2.onmicrosoft.com).
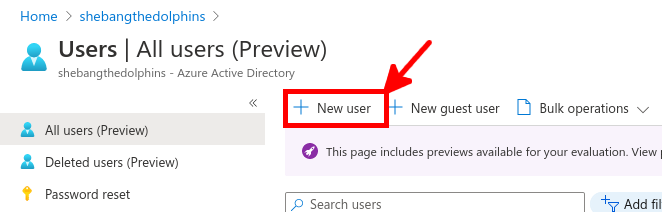

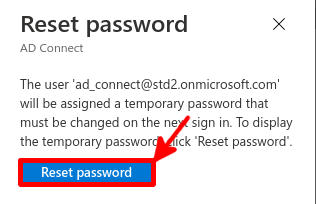
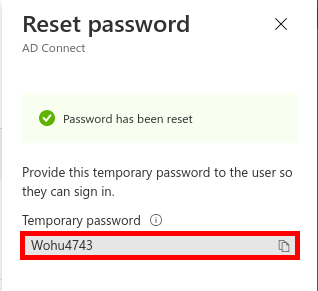

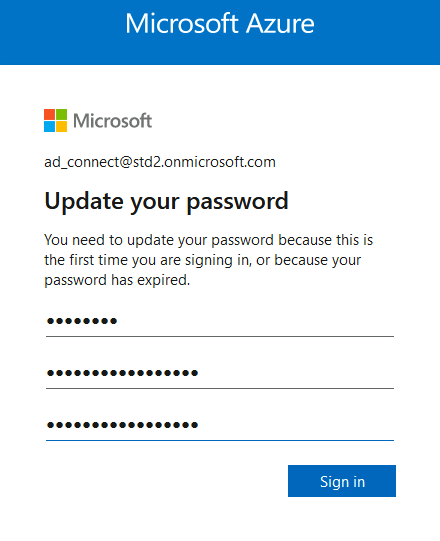
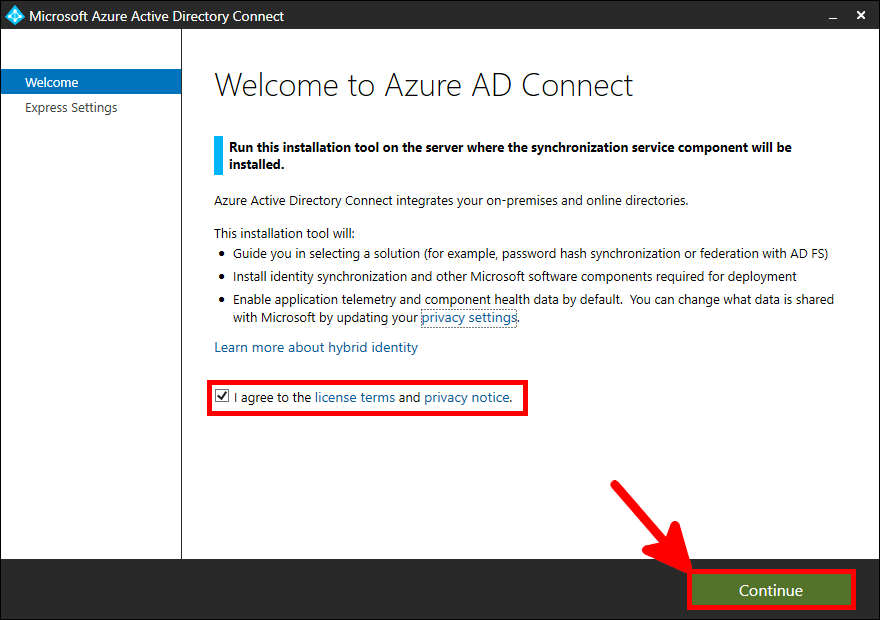
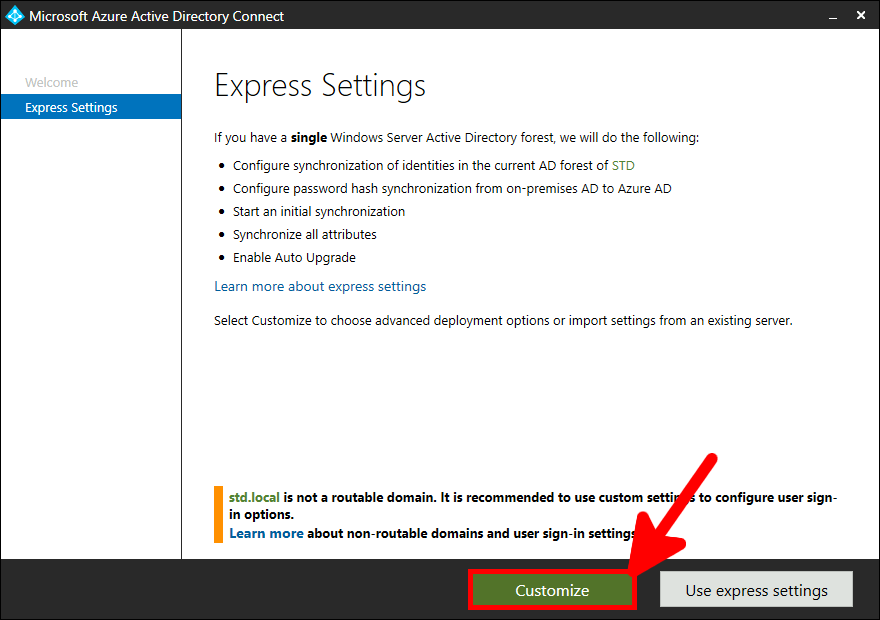
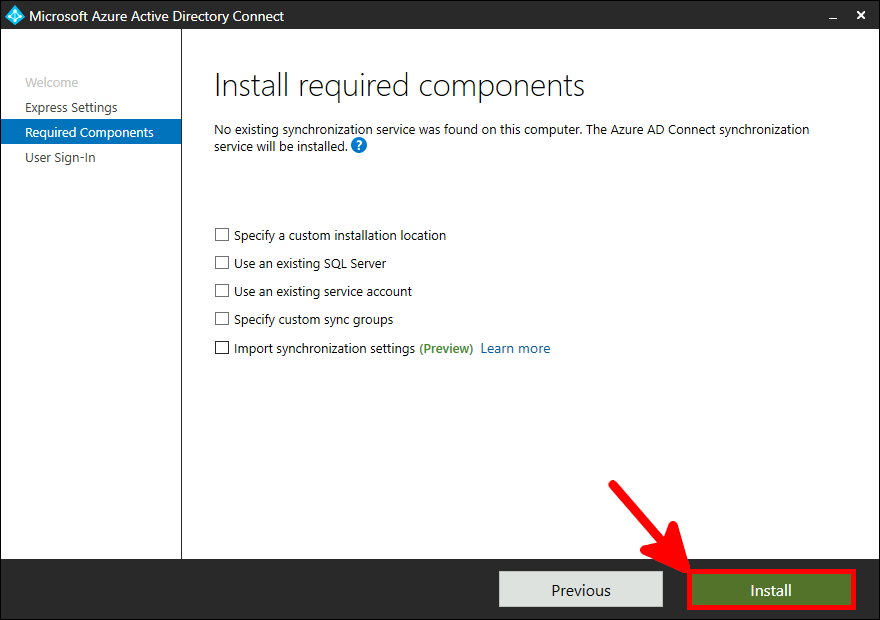
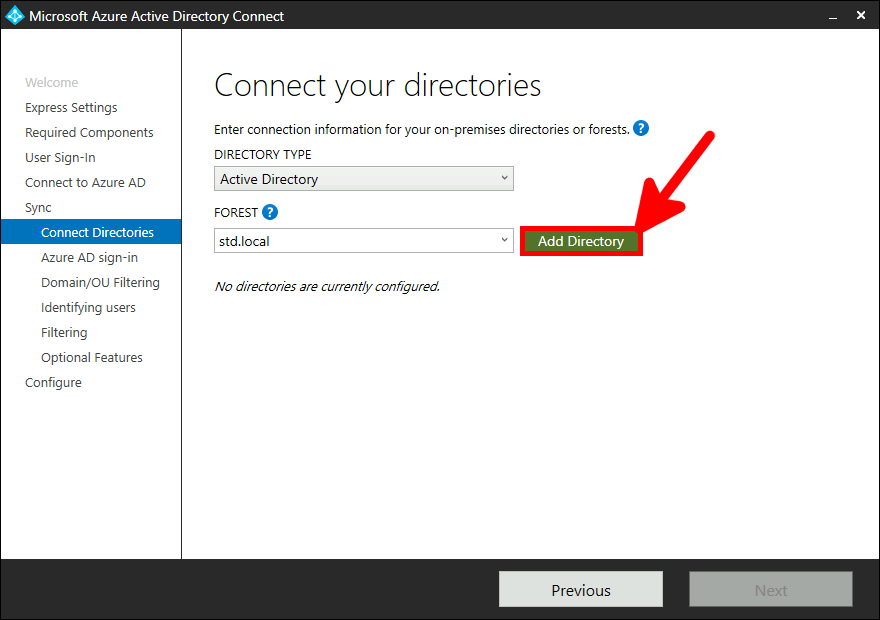
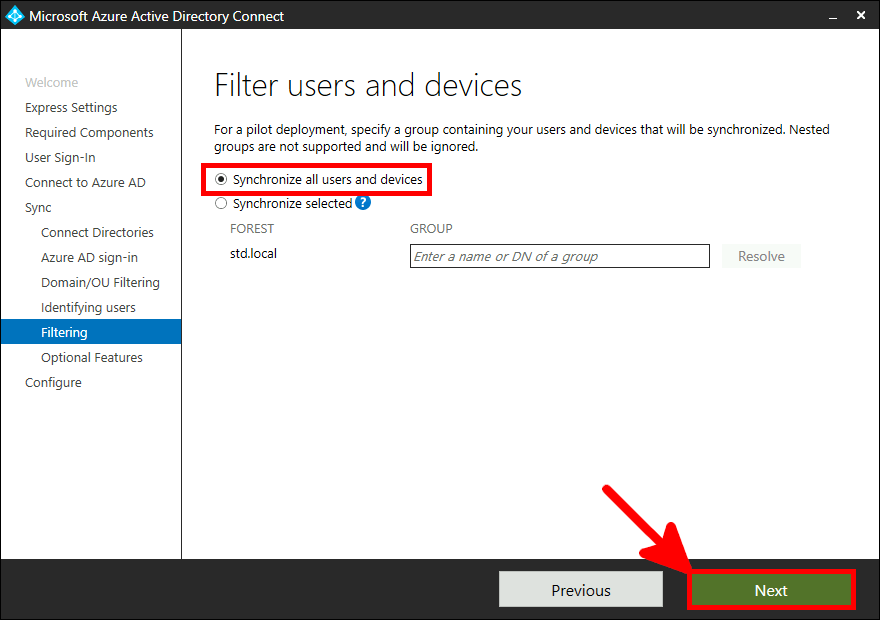
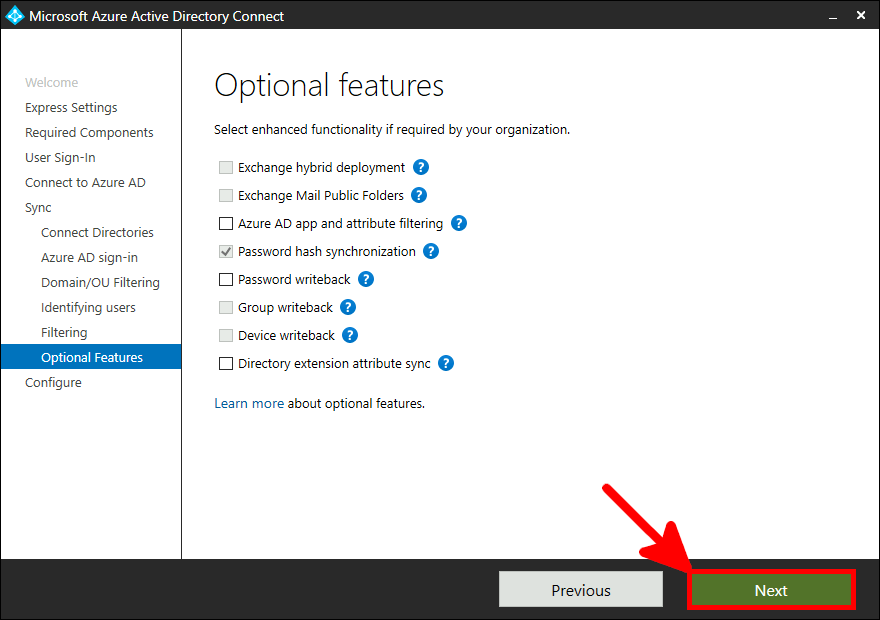
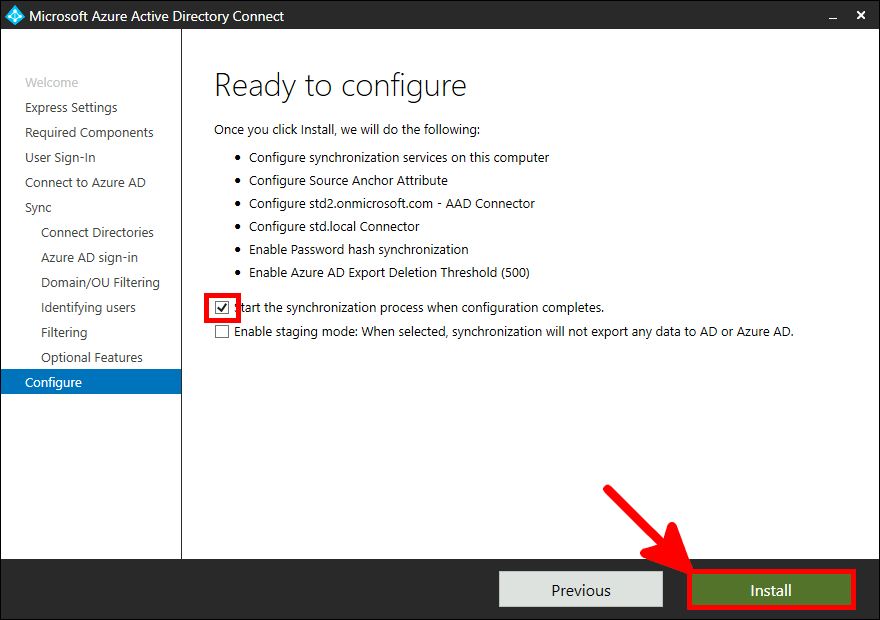
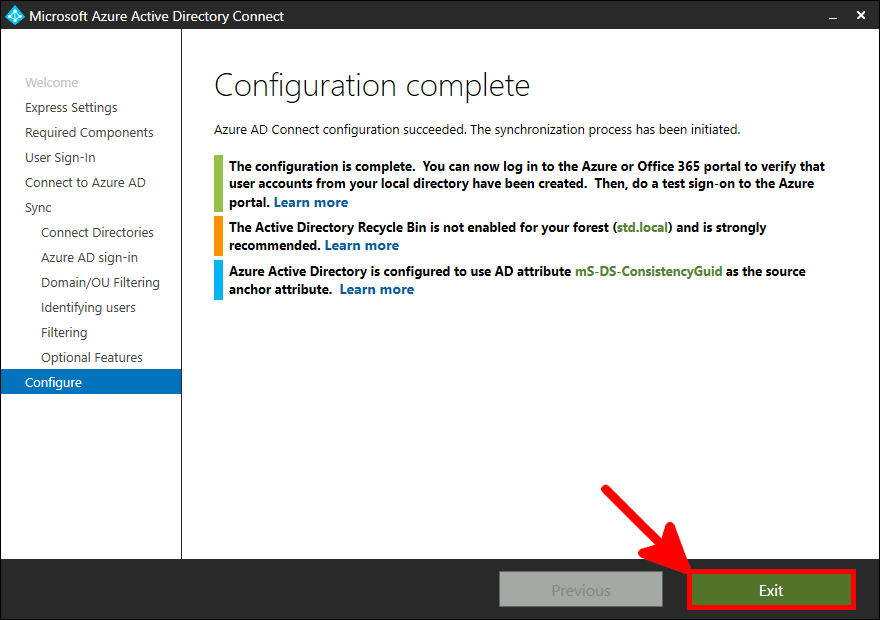
Now we need to install and configure AD Connect. This software is used to synchronize our AD local users to our AD Azure infrastructure.
This software needs to be installed once, on a AD server.
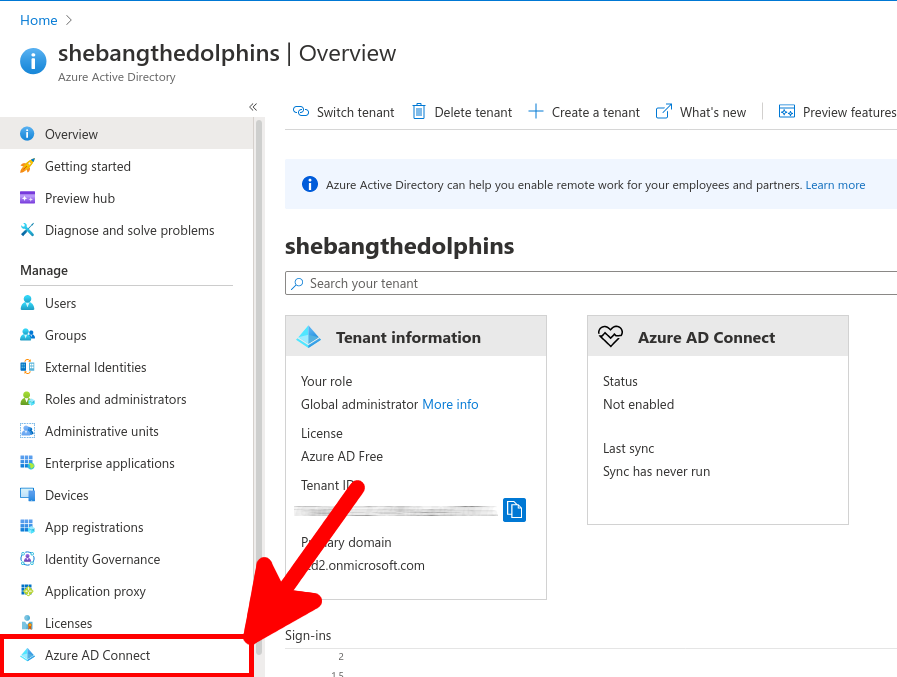
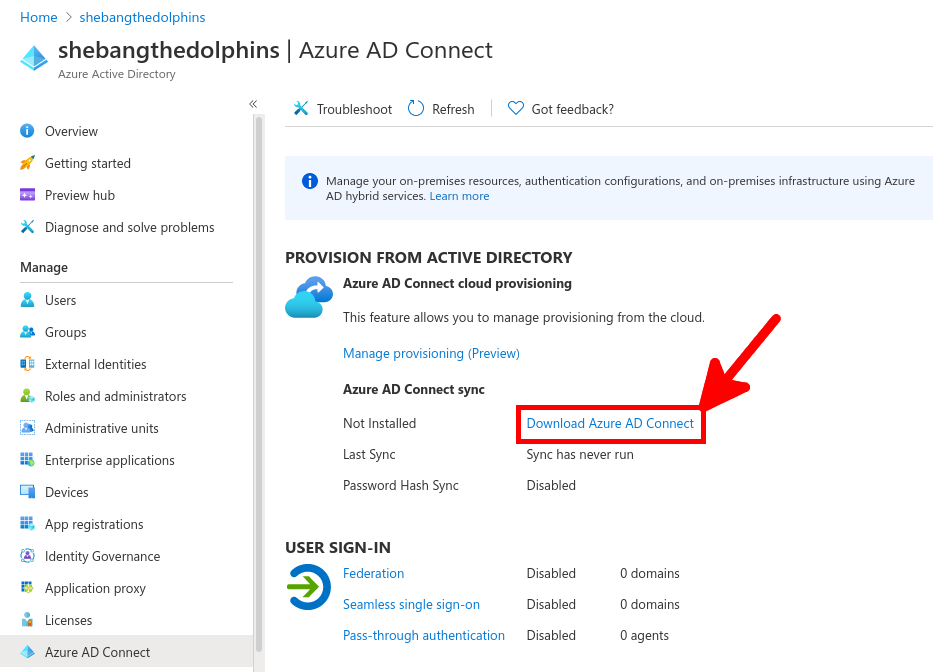
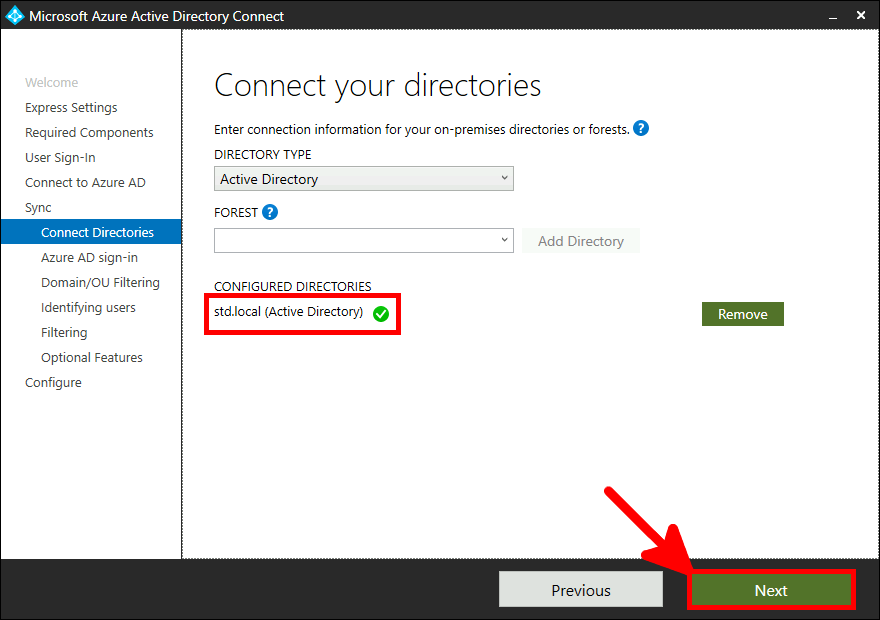
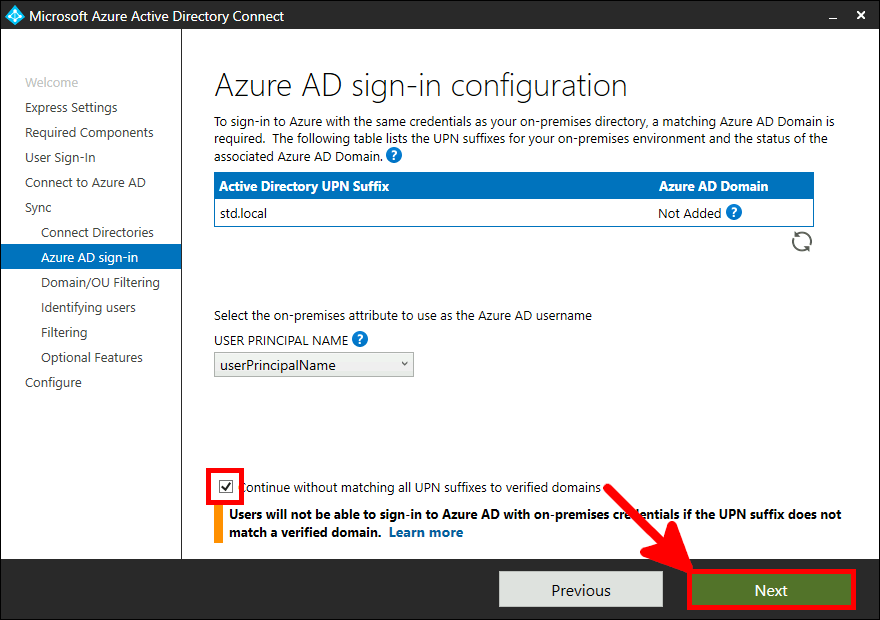
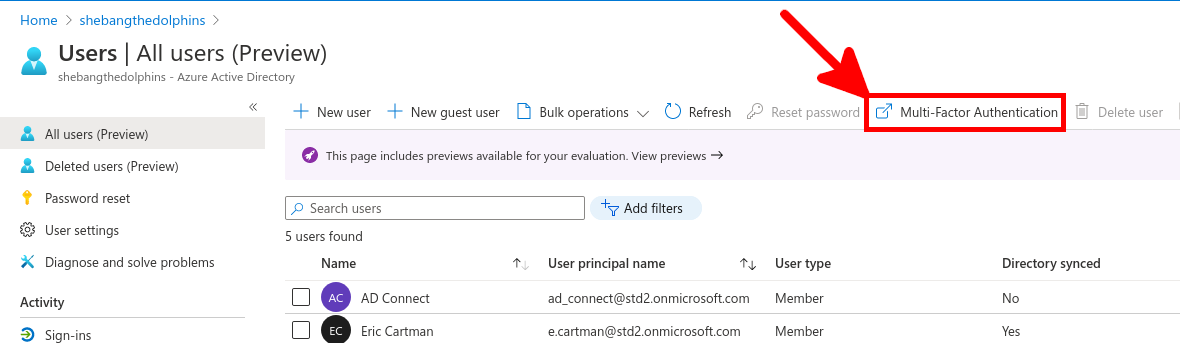
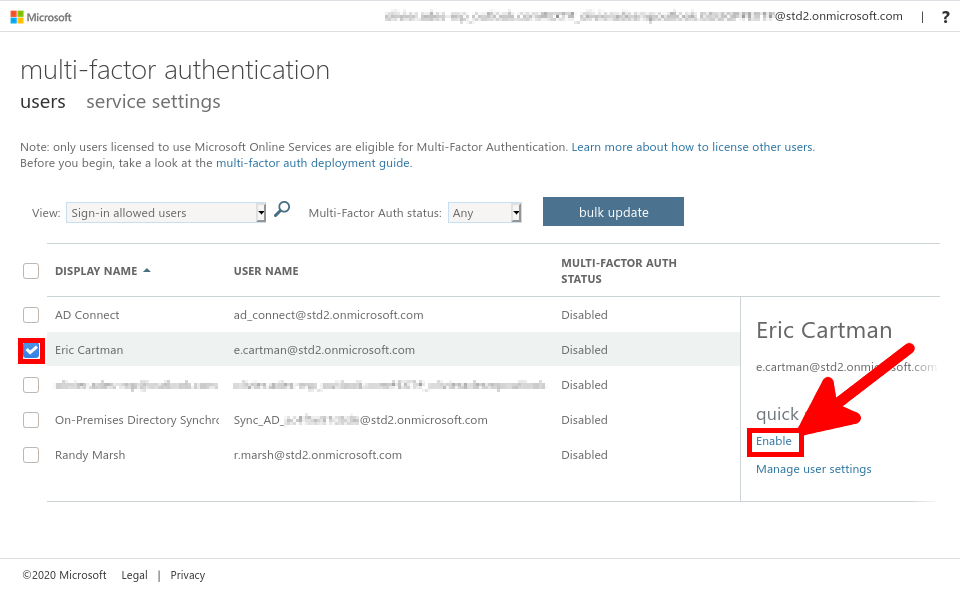
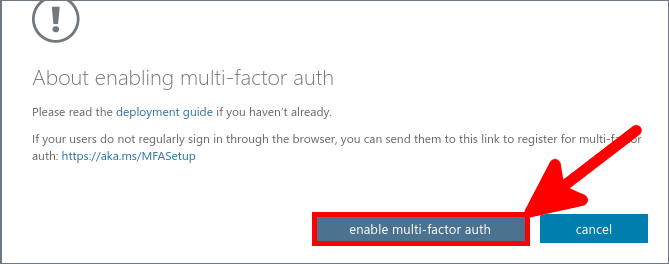
Go back to Azure portal, to enable MFA.
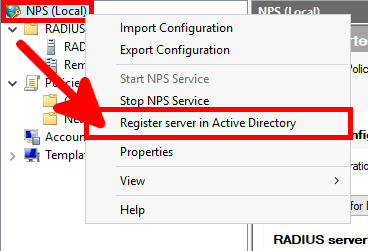
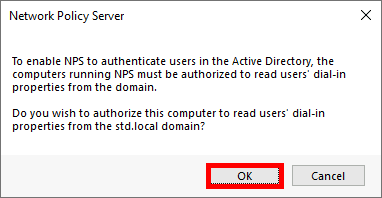
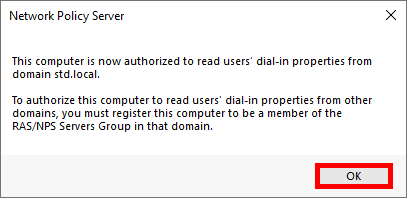
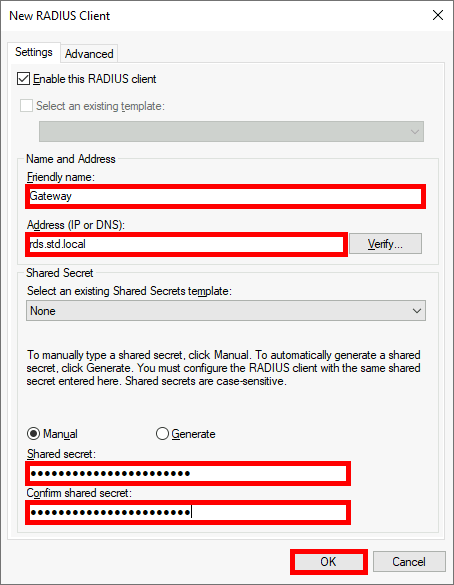
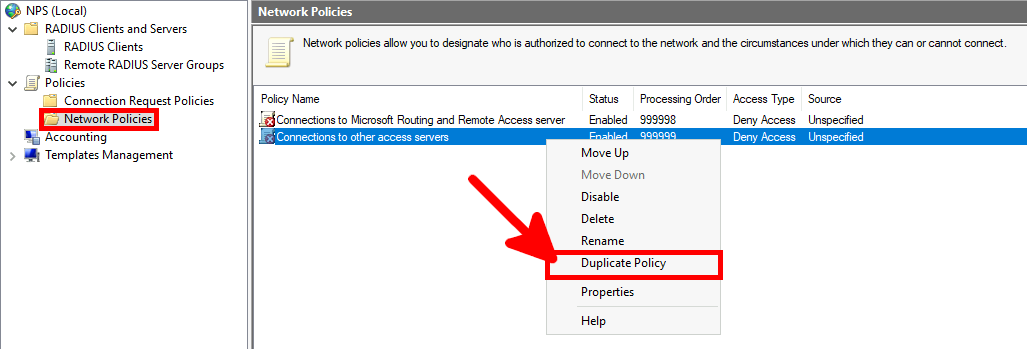
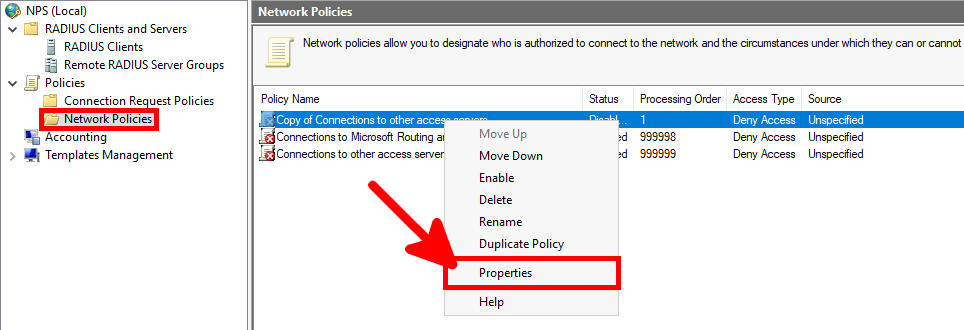
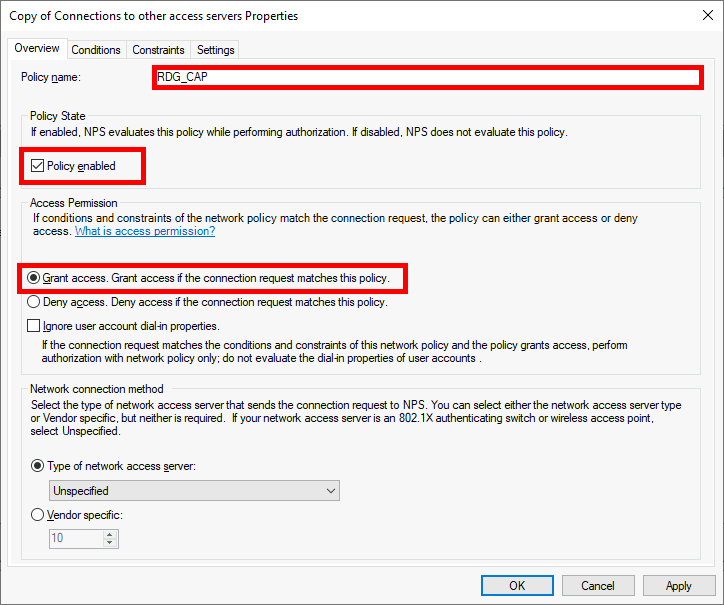
We need a NPS server, it could be installed on the AD server but in this guide I will install it on a brand new virtual machine.
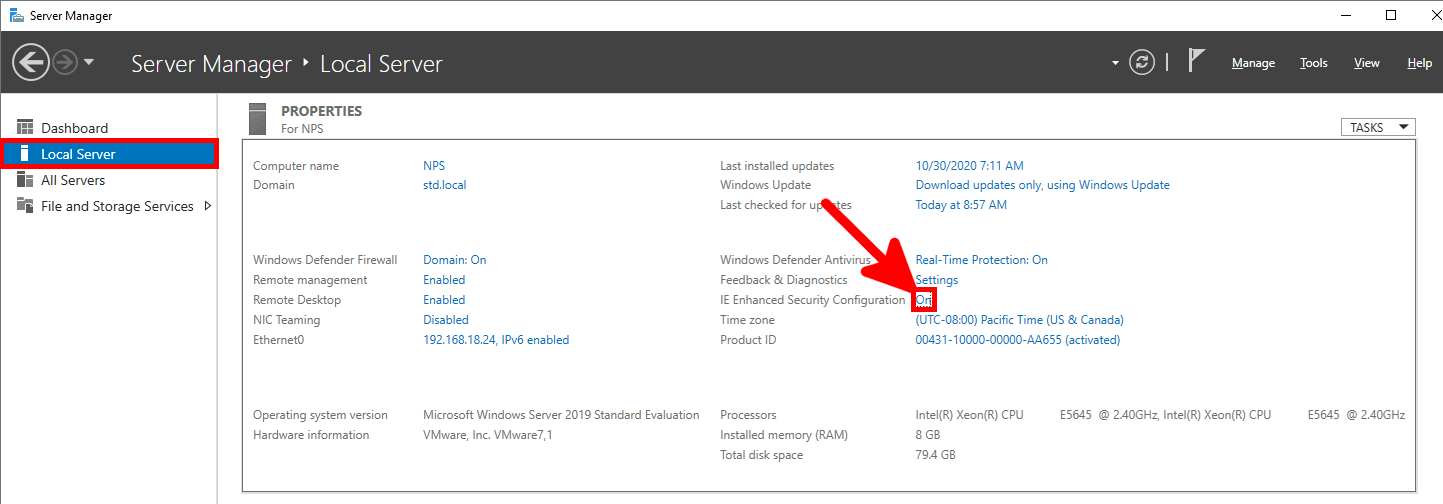
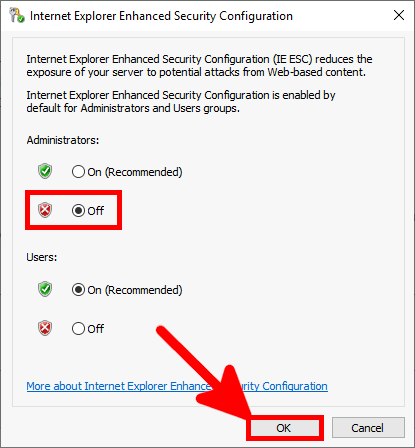
I recommend to (temporarily) disable IE Enhanced Security because it can prevent the Azure authentication to work during the AzureMfaNpsExtnConfigSetup PowerShell script execution.
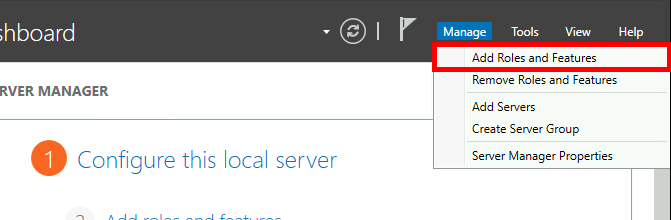
We can choose to install NPS role with PowerShell or via Graphical User Interface.
PS C:\Users\administrator.STD> Install-WindowsFeature NPAS -Restart -IncludeManagementTools
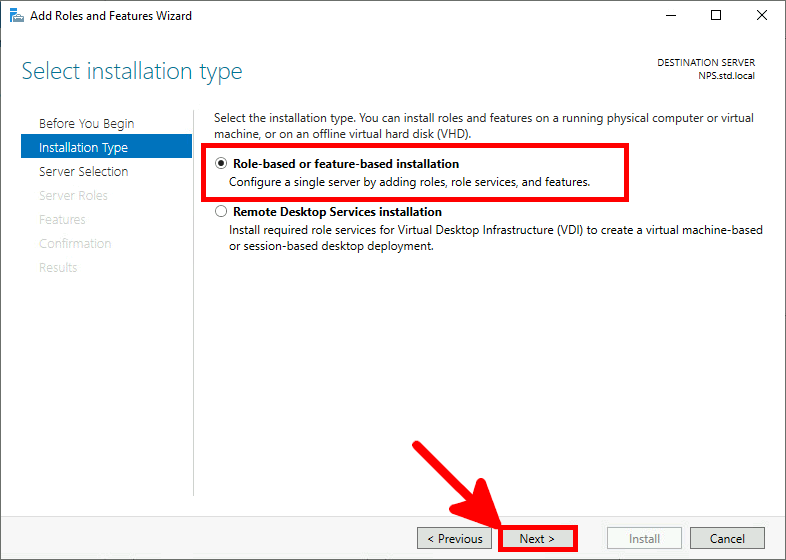
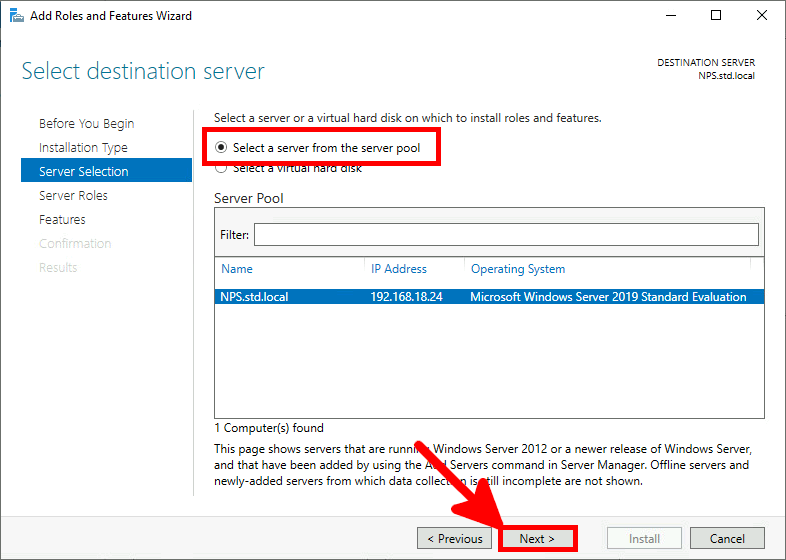
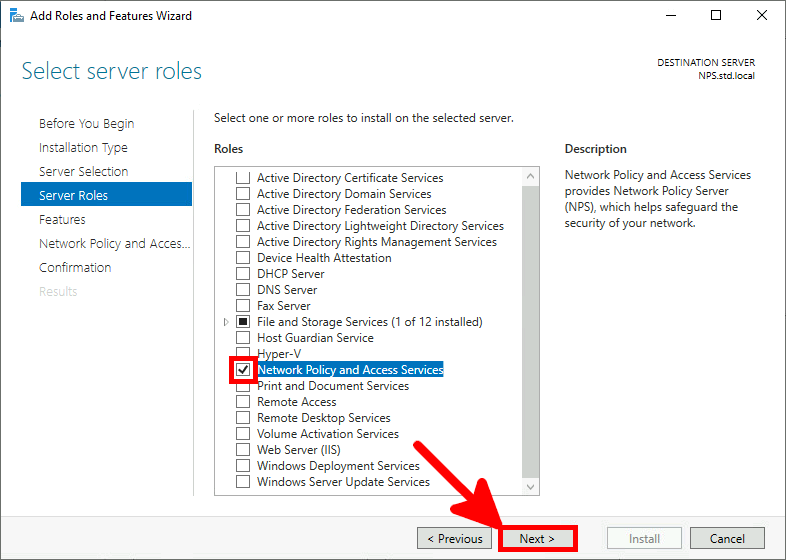
It's a module which allows to add cloud-based MFA capabilities. It will directly communicate with Azure AD infrastructure.
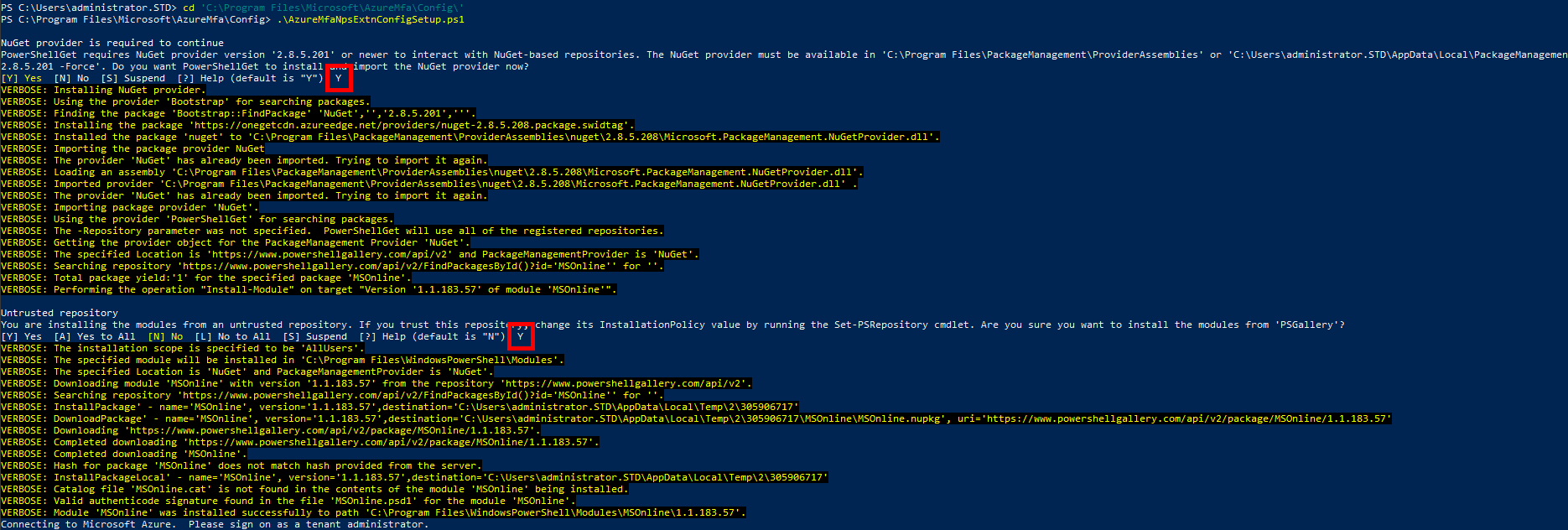
Now we need to execute the AzureMfaNpsExtnConfigSetup.ps1 PowerShell script in order to configure certificates which will be used by the NPS extension.
PS C:\Users\administrator.STD> cd 'c:\Program Files\Microsoft\AzureMfa\Config'
PS C:\Users\administrator.STD> .\AzureMfaNpsExtnConfigSetup.ps1

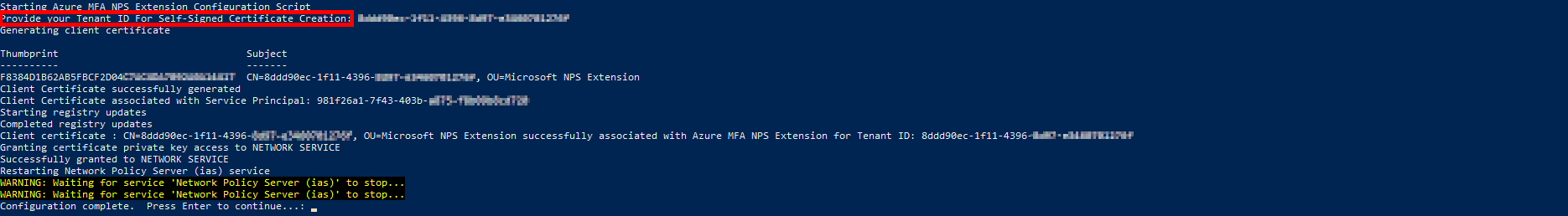
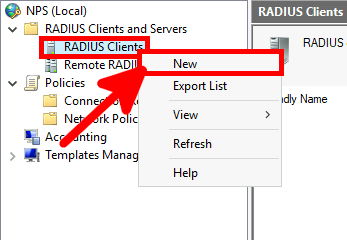
It seems that Windows (I tried on a Windows Server 2019) doesn't automatically open RADIUS ports. So, create a firewall rule to open incomming udp 1812, udp 1813, udp 1645, udp 1646.
PS C:\Users\administrator.STD> netsh advfirewall firewall add rule name="NPS" dir=in localport=1812,1813,1645,1646 remoteport=0-65535 protocol=UDP action=allow remoteip=any localip=any
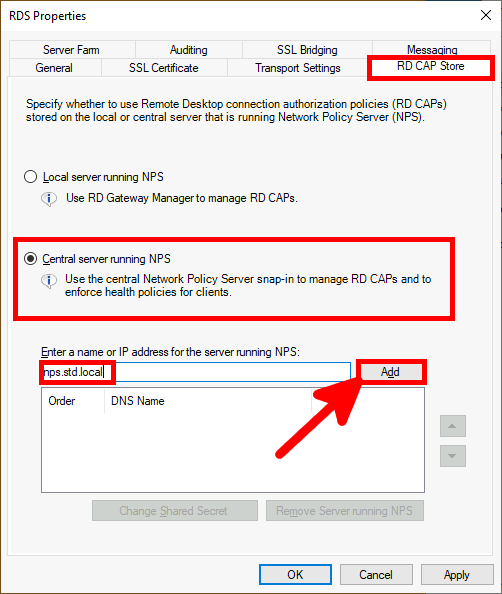
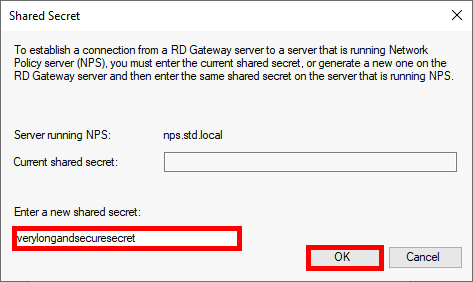
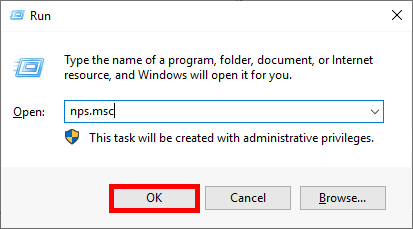
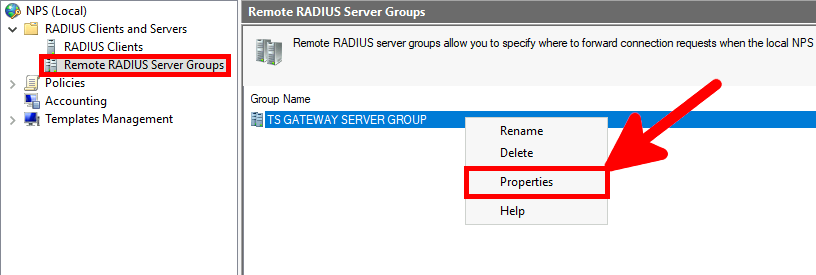
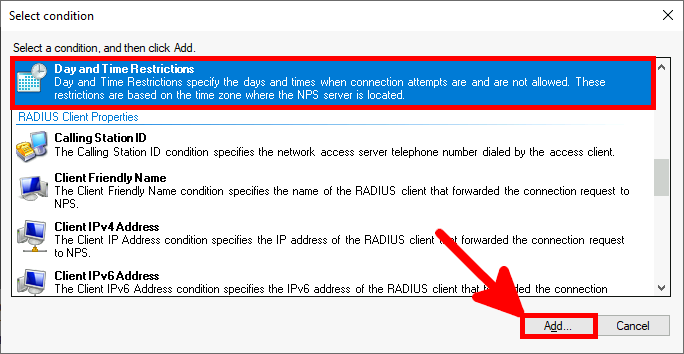
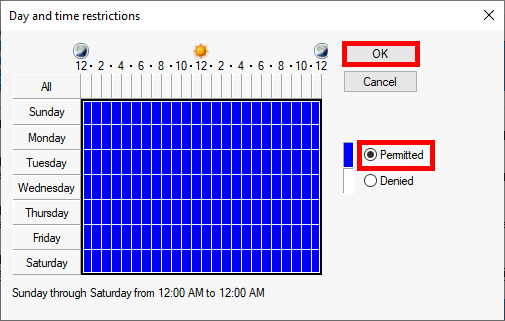
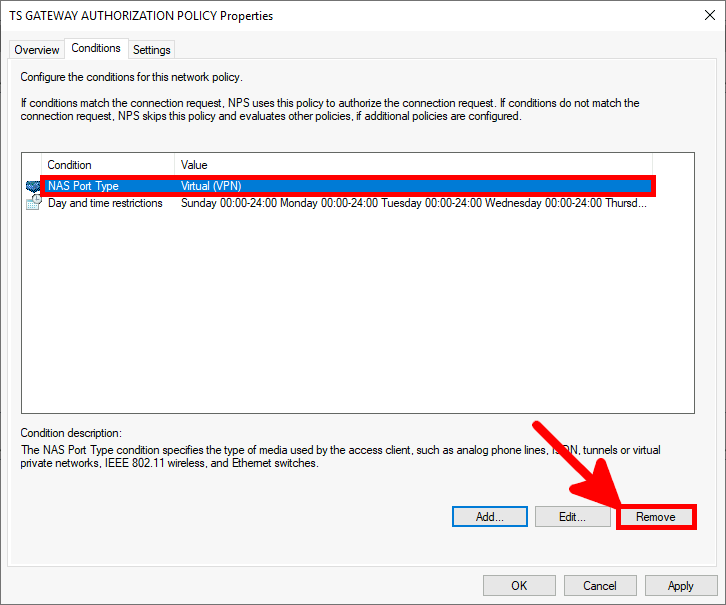
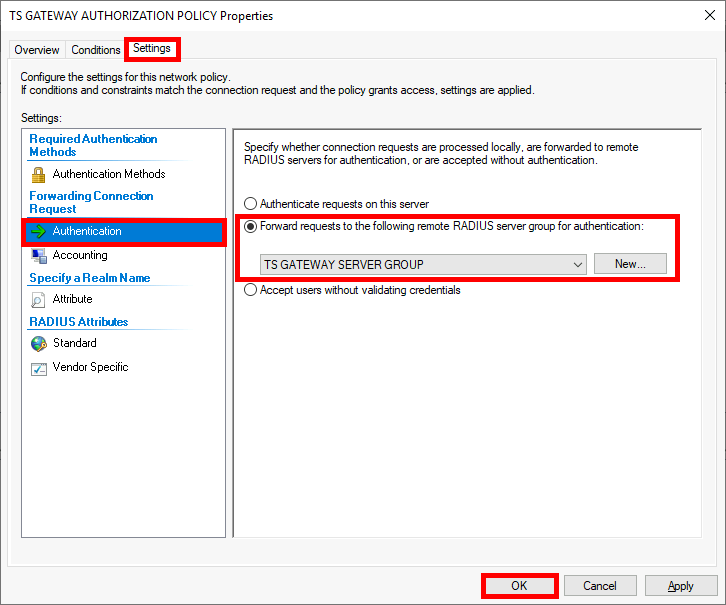

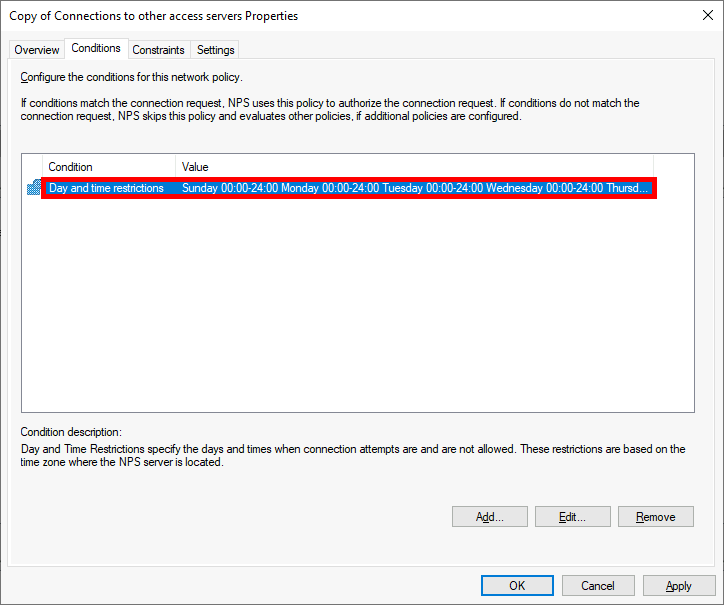
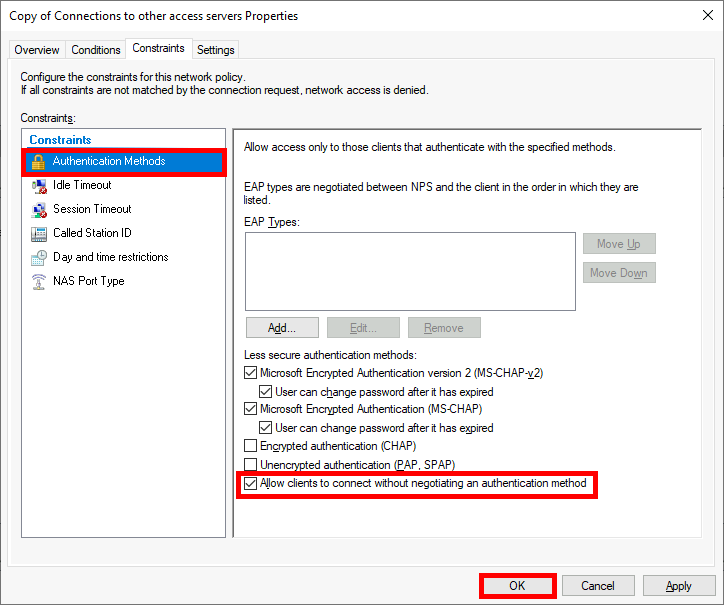
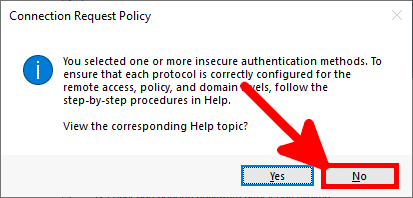
Microsoft Authenticator is a Android and iOS phone app. It allows two factor authentication by using a phone.
Install the App from any store you want.
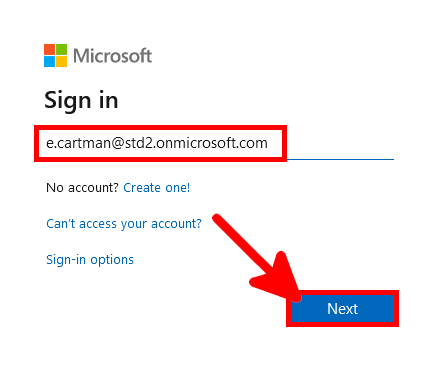
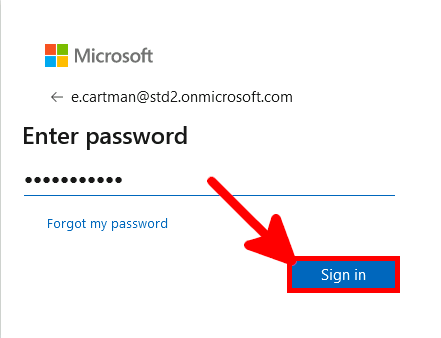
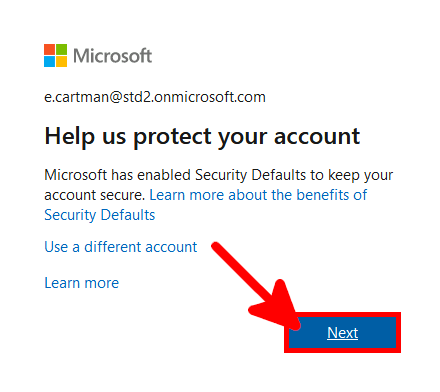
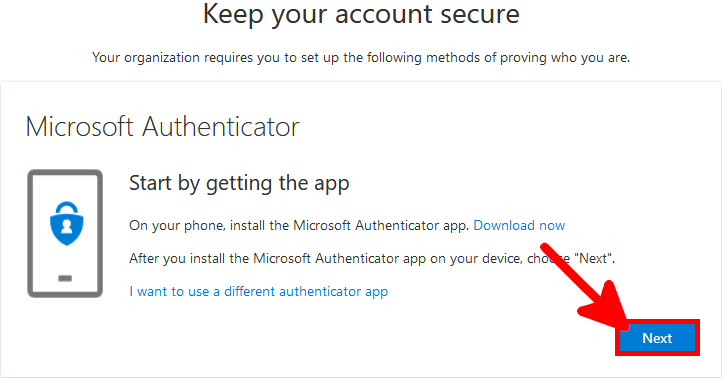
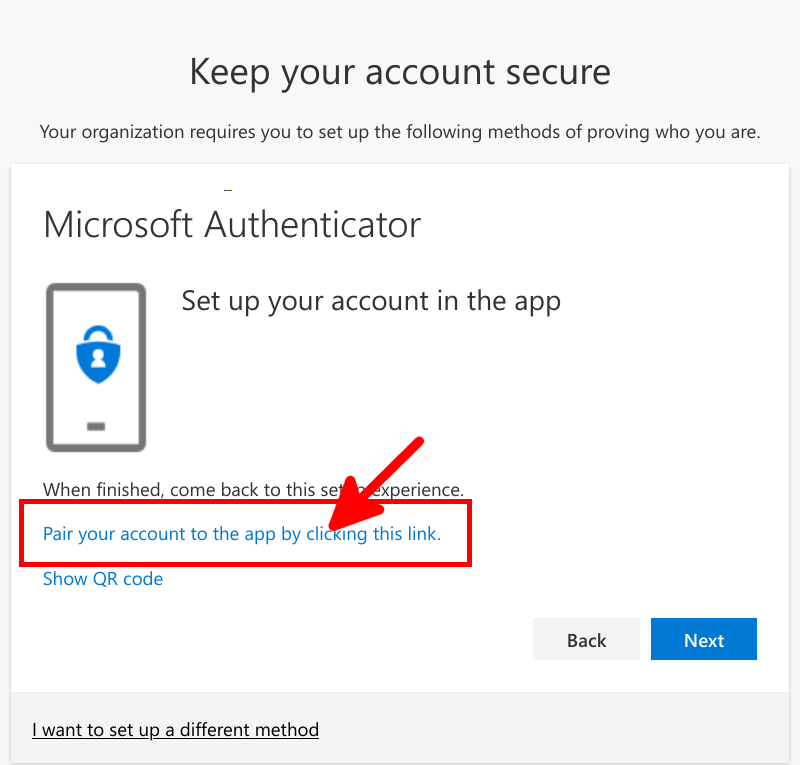
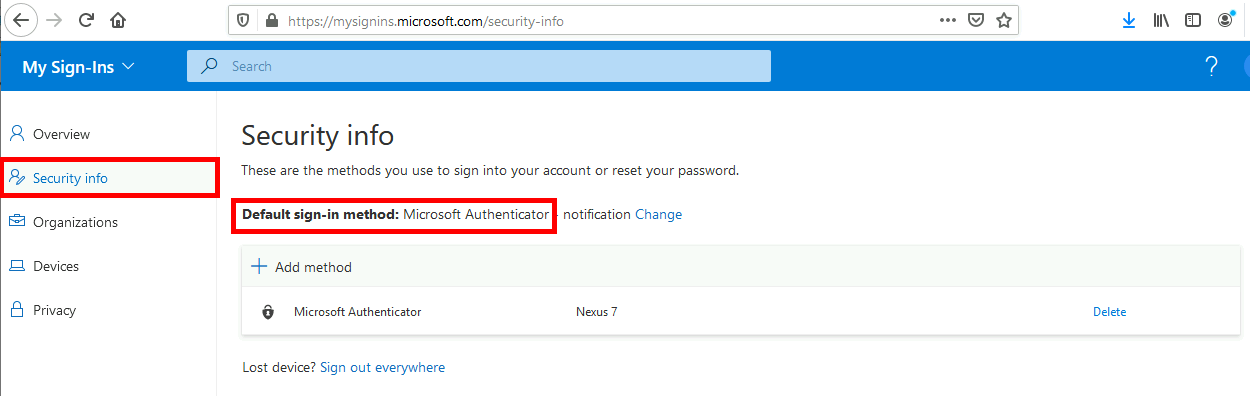
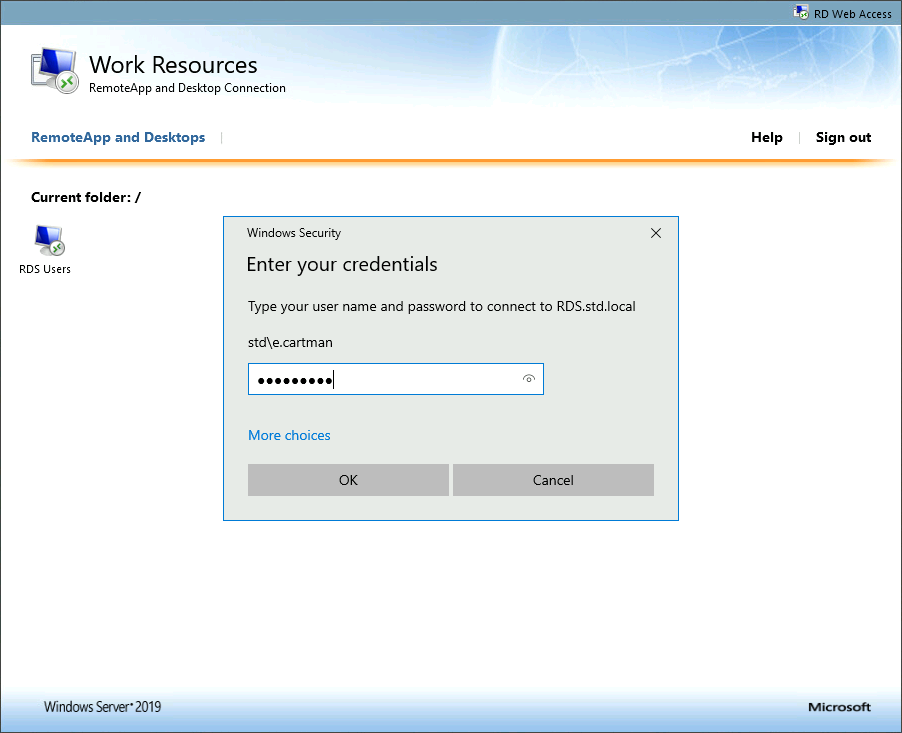
We need to check that our default authentication method is Microsoft Authenticator otherwise MFA could send SMS to authenticate, which can't be used to allow RDS connection.
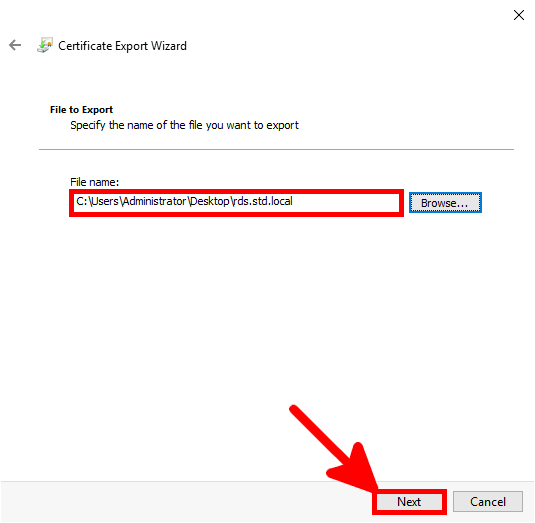
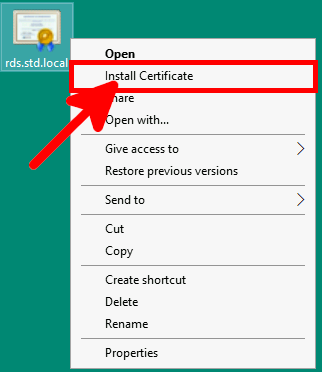
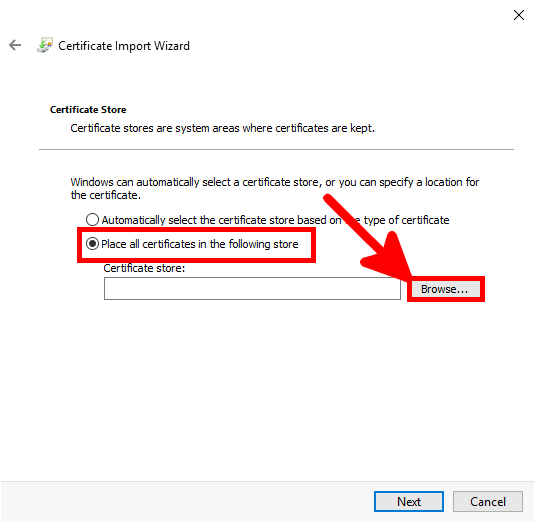
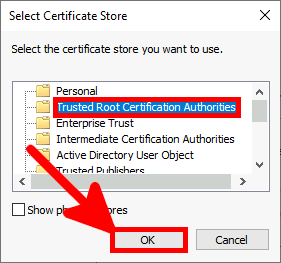
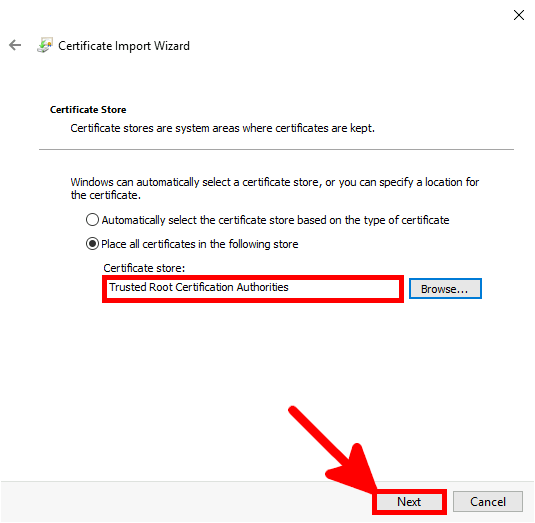
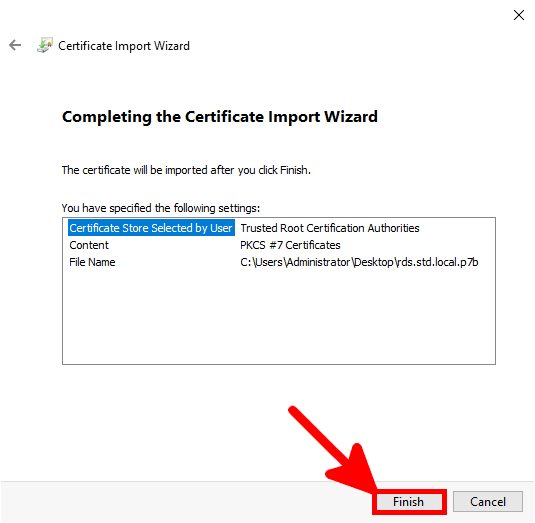

Contact :