root@host:~# apt-get install ipsec-tools
$ dd if=/dev/random count=16 bs=1| xxd -ps a9b3d99cd41ed7bc51e1a007c1ccc97f 16+0 enregistrements lus 16+0 enregistrements écrits $ dd if=/dev/random count=24 bs=1| xxd -ps 2d619f669e2a93d69c286546bf3f8c2cc22853eac945ed06 24+0 enregistrements lus 24+0 enregistrements écrits
#!/usr/sbin/setkey -f ## Flush the SAD and SPD # flush; spdflush; ## AH security association (SA) #alice et bob add 192.168.0.84 192.168.0.95 ah 10000 -A hmac-md5 "1234567890123456"; add 192.168.0.95 192.168.0.84 ah 20000 -A hmac-md5 "1234567890123456"; #ESP #alice et bob add 192.168.0.84 192.168.0.95 esp 10001 -E 3des-cbc 0x2d619f669e2a93d69c286546bf3f8c2cc22853eac945ed06; #on peut choisir des clés différentes (entre Alice et Bob et Bob et Alice) : add 192.168.0.95 192.168.0.84 esp 20001 -E 3des-cbc "123456789012345678901234"; ## security policy #alice et bob spdadd 192.168.0.84 192.168.0.95 any -P out ipsec esp/transport//require ah/transport//require; spdadd 192.168.0.95 192.168.0.84 any -P in ipsec esp/transport//require ah/transport//require;
#!/usr/sbin/setkey -f ## Flush the SAD and SPD # flush; spdflush; ## AH security association (SA) add 192.168.0.84 192.168.0.95 ah 10000 -A hmac-md5 "1234567890123456"; add 192.168.0.84 192.168.0.95 esp 10001 -E 3des-cbc 0x9d6c4a8275ab12fbfdcaf01f0ba9dcfb5f424c878e97f888; add 192.168.0.95 192.168.0.84 ah 20000 -A hmac-md5 "1234567890123456"; add 192.168.0.95 192.168.0.84 esp 20001 -E 3des-cbc "123456789012345678901234"; spdadd 192.168.0.95 192.168.0.84 any -P out ipsec esp/transport//require ah/transport//require; spdadd 192.168.0.84 192.168.0.95 any -P in ipsec esp/transport//require ah/transport//require;
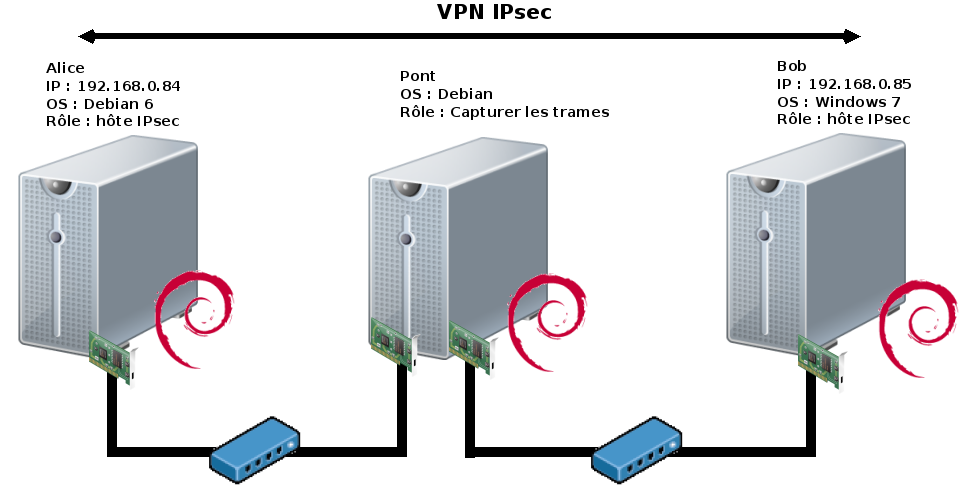
On peut voir que les trames qui traversent notre pont comportent bien les champs ESP et AH.
root@host:~# tcpdump -i br0 11:59:39.230708 IP 192.168.0.95 > 192.168.0.84: AH(spi=0x00004e20,seq=0x68d): ESP(spi=0x00004e21,seq=0x68d), length 88 11:59:39.328125 IP 192.168.0.84 > 192.168.0.95: AH(spi=0x00002710,seq=0x746): ESP(spi=0x00002711,seq=0x746), length 88 11:59:39.328307 IP 192.168.0.95 > 192.168.0.84: AH(spi=0x00004e20,seq=0x68e): ESP(spi=0x00004e21,seq=0x68e), length 88 11:59:40.230594 IP 192.168.0.84 > 192.168.0.95: AH(spi=0x00002710,seq=0x747): ESP(spi=0x00002711,seq=0x747), length 88 11:59:40.230949 IP 192.168.0.95 > 192.168.0.84: AH(spi=0x00004e20,seq=0x68f): ESP(spi=0x00004e21,seq=0x68f), length 88 11:59:40.327423 IP 192.168.0.84 > 192.168.0.95: AH(spi=0x00002710,seq=0x748): ESP(spi=0x00002711,seq=0x748), length 88 11:59:40.327760 IP 192.168.0.95 > 192.168.0.84: AH(spi=0x00004e20,seq=0x690): ESP(spi=0x00004e21,seq=0x690), length 88 11:59:41.231482 IP 192.168.0.84 > 192.168.0.95: AH(spi=0x00002710,seq=0x749): ESP(spi=0x00002711,seq=0x749), length 88 11:59:41.231717 IP 192.168.0.95 > 192.168.0.84: AH(spi=0x00004e20,seq=0x691): ESP(spi=0x00004e21,seq=0x691), length 88 11:59:41.326445 IP 192.168.0.84 > 192.168.0.95: AH(spi=0x00002710,seq=0x74a): ESP(spi=0x00002711,seq=0x74a), length 88 11:59:41.326686 IP 192.168.0.95 > 192.168.0.84: AH(spi=0x00004e20,seq=0x692): ESP(spi=0x00004e21,seq=0x692), length 88 11:59:42.230489 IP 192.168.0.84 > 192.168.0.95: AH(spi=0x00002710,seq=0x74b): ESP(spi=0x00002711,seq=0x74b), length 88
setkey -f /etc/ipsec-tools.conf
racoon -F -f /etc/racoon/racoon.conf
setkey -F
setkey -D
setkey -DP
Contact :